Netskope named a Leader in the 2024 Gartner® Magic Quadrant™ for Security Service Edge. Get the report
-
Why Netskope
- Why Netskope
Why Netskope
Changing the way networking and security work together.
Get the reportStill Highest in Execution.
Still Furthest in Vision.Learn why 2024 Gartner® Magic Quadrant™ named Netskope a Leader for Security Service Edge the third consecutive year.
- Why Netskope
Our Customers
Netskope serves more than 3,000 customers worldwide including more than 25 of the Fortune 100
See our customersWe help our customers to be Ready for Anything - Why Netskope
Our Partners
We partner with security leaders to help you secure your journey to the cloud.
Learn about Netskope PartnersNetskope’s partner-centric go-to-market strategy enables our partners to maximize their growth and profitability while transforming enterprise security.
-
Platform
- Platform
Netskope One Platform
Netskope One is a converged security and network as a service platform.
Get the white paperYour Network of TomorrowPlan your path toward a faster, more secure, and more resilient network designed for the applications and users that you support.
- Platform
Netskope One Platform Features
Netskope One powers greater business agility with lightning speed and dependable resilience.
Learn about Netskope OneIntroducing the Netskope One PlatformNetskope One is a cloud-native platform that offers converged security and networking services to enable your SASE and zero trust transformation.
- Platform
NewEdge
NewEdge is the world’s largest, highest-performing security private cloud.
Learn about NewEdgeEmbrace a Secure Access Service Edge (SASE) architectureNetskope NewEdge is the world’s largest, highest-performing security private cloud and provides customers with unparalleled service coverage, performance and resilience.
- Platform
Technology Partners & Integrations
Netskope partners with the strongest companies in enterprise technology.
Learn about Cloud ExchangeNetskope Cloud ExchangeThe Netskope Cloud Exchange (CE) provides customers with powerful integration tools to leverage investments across their security posture.
-
Products
- Products
Security Service Edge Products
Protect against advanced and cloud-enabled threats and safeguard data across all vectors.
Go to Products OverviewThe platform of the future is NetskopeIntelligent Security Service Edge (SSE), Cloud Access Security Broker (CASB), Cloud Firewall, Next Generation Secure Web Gateway (SWG), and Private Access for ZTNA built natively into a single solution to help every business on its journey to Secure Access Service Edge (SASE) architecture.
- Security Service Edge (SSE)
- Next Gen Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- ZTNA Next
- SkopeAI
- Public Cloud Security
- Advanced Analytics
- Cloud Firewall
- Data Loss Prevention (DLP)
- Proactive Digital Experience Management
- Device Intelligence
- Remote Browser Isolation
- SaaS Security Posture Management
- Security Service Edge (SSE)
- Products
Borderless SD-WAN
Confidently provide secure, high-performance access to every remote user, device, site, and cloud.
Learn about Next Gen SASE BranchNext Gen SASE Branch is hybrid — connected, secured, and automatedNetskope Next Gen SASE Branch converges Context-Aware SASE Fabric, Zero-Trust Hybrid Security, and SkopeAI-powered Cloud Orchestrator into a unified cloud offering, ushering in a fully modernized branch experience for the borderless enterprise.
- Borderless SD-WAN
- Next Gen SASE Branch
- Secure SD-WAN
- Endpoint SD-WAN
- Micro Branch
- Wireless WAN
- Multi-Cloud Networking
- IoT Intelligent Access
- Borderless SD-WAN
- Products
Secure Access Service Edge
Netskope One SASE provides a cloud-native, fully-converged and single-vendor SASE solution.
Get the eBookDesigning a SASE Architecture For DummiesGet your complimentary copy of the only guide to SASE design you’ll ever need.
-
Solutions
- Solutions
Network Transformation
Achieve agility and efficiency through digital transformation.
Go to Solutions OverviewLearn about NewEdgeMake the move to market-leading cloud security services with minimal latency and high reliability. - Solutions
Security modernization
Meet the security challenges of today and tomorrow.
Learn how we secure generative AI useSafely enable the use of generative AI applications with application access control, real-time user coaching, and best-in-class data protection.- Advanced Threat Protection
- Data Protection
- Hybrid Work
- Insider Risk
- Maintain Cloud Compliance
- Replace VPNs
- Safely Enable ChatGPT and Generative AI
- Secure Managed Cloud Applications
- Secure Unmanaged Cloud Services
- AWS, Azure & GCP
- Advanced Threat Protection
- Solutions
Frameworks
Embrace the regulatory frameworks shaping cybersecurity.
Go to Solutions OverviewLearn about Zero TrustZero trust solutions for SSE and SASE deployments - Solutions
Government and Industries
Netskope helps the largest agencies and enterprises in the world secure their journey to the cloud.
Learn about Netskope GovCloudNetskope achieves FedRAMP High AuthorizationChoose Netskope GovCloud to accelerate your agency’s transformation.
- Financial Services and Insurance
- Healthcare and Life Sciences
- High Technology
- Higher Education Institutions
- K12
- Legal
- Manufacturing
- Public Sector
- Retail and Hospitality
- Service Companies
- Utilities
- Financial Services and Insurance
-
Resources
- Resources
Resources
Learn more about how Netskope can help you secure your journey to the cloud.
Play the podcastSecurity Visionaries PodcastHow to Use a Magic Quadrant and Other Industry Research
In this episode Max Havey, Steve Riley and Mona Faulkner dissect the intricate process of creating a Magic Quadrant and why it's much more than just a chart. - Resources
Blog
Learn how Netskope enables security and networking transformation through security service edge (SSE)
Read the blogLatest BlogsRead how Netskope can enable the Zero Trust and SASE journey through security service edge (SSE) capabilities.
- Resources
Events and Workshops
Stay ahead of the latest security trends and connect with your peers.
Explore sessionsSASE Week 2023: Your SASE journey starts now!Replay sessions from the fourth annual SASE Week.
- Resources
Security Defined
Everything you need to know in our cybersecurity encyclopedia.
Learn about Security Service EdgeWhat is Security Service Edge?Explore the security side of SASE, the future of network and protection in the cloud.
- Security Defined overview
- What is SASE?
- What is Security Service Edge?
- What is a Cloud Access Security Broker (CASB)?
- What is Zero Trust Security?
- What is a Next Generation Secure Web Gateway (SWG)?
- What is Data Loss Prevention (DLP)?
- What is SD-WAN?
- What is Generative AI?
- What is Remote Browser Isolation (RBI)?
- What is SSPM?
- What is FedRamp?
- Security Defined overview
-
Company
- Company
Company
We help you stay ahead of cloud, data, and network security challenges.
Find out moreSupporting sustainability through data securityNetskope is proud to participate in Vision 2045: an initiative aimed to raise awareness on private industry’s role in sustainability.
- Company
Leadership
Our leadership team is fiercely committed to doing everything it takes to make our customers successful.
Meet our teamThinkers, builders, dreamers, innovators. Together, we deliver cutting-edge cloud security solutions to help our customers protect their data and people. - Company
Customer Solutions
We are here for you and with you every step of the way, ensuring your success with Netskope.
Learn about Professional ServicesNetskope’s talented and experienced Professional Services team provides a prescriptive approach to your successful implementation.- Professional Services
- Customer Success
- Technical Support
- Service Delivery Partners
- Customer Community
- Product Documentation
- Support Portal
- Trust Portal
- Professional Services
- Company
Training and Certification
Netskope training will help you become a cloud security expert.
Learn about Training and CertificationsSecure your digital transformation journey and make the most of your cloud, web, and private applications with Netskope training.- Netskope Security Cloud Introductory Online Technical Training
- Netskope Security Cloud Operation and Administration (NSCO&A)
- Netskope Security Cloud Implementation and Integration (NSCI&I)
- Netskope Cloud Security Certification Program
- Netskope Security Cloud Introductory Online Technical Training
- Why Netskope
Changing the way networking and security work together.
- Our Customers
Netskope serves more than 3,000 customers worldwide including more than 25 of the Fortune 100
- Our Partners
We partner with security leaders to help you secure your journey to the cloud.
Still Furthest in Vision.
Learn why 2024 Gartner® Magic Quadrant™ named Netskope a Leader for Security Service Edge the third consecutive year.
Get the report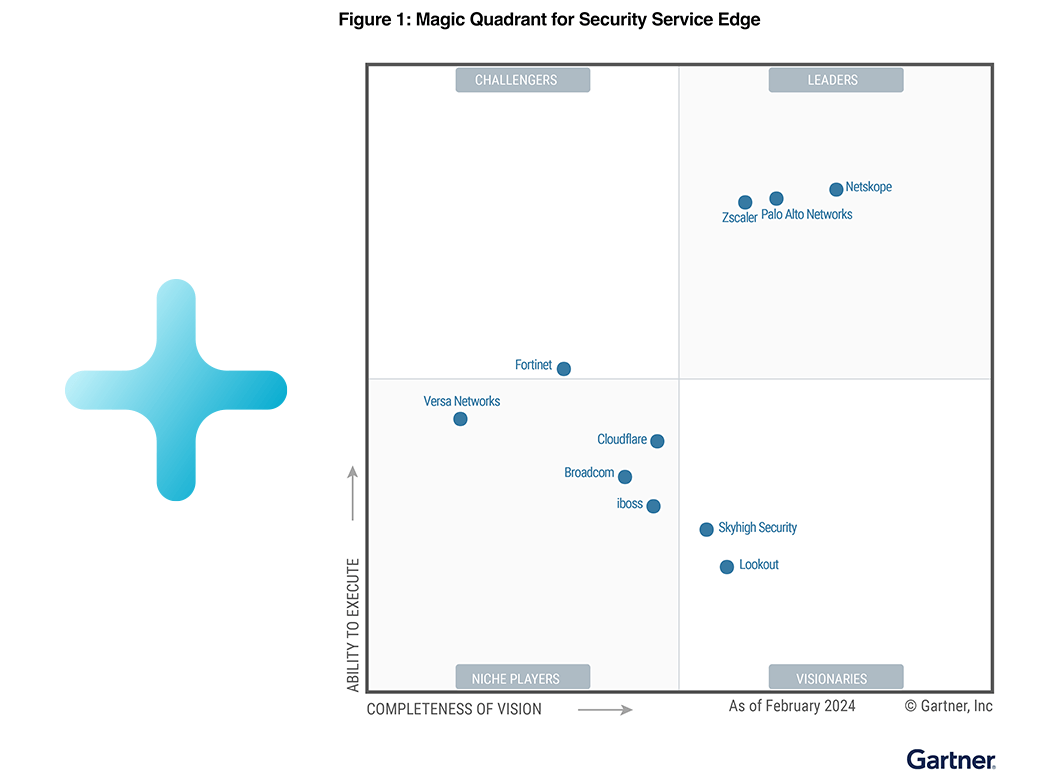

- Netskope One Platform
Netskope One is a converged security and network as a service platform.
- Netskope One Platform Features
Netskope One powers greater business agility with lightning speed and dependable resilience.
- NewEdge
NewEdge is the world’s largest, highest-performing security private cloud.
- Technology Partners & Integrations
Netskope partners with the strongest companies in enterprise technology.
Plan your path toward a faster, more secure, and more resilient network designed for the applications and users that you support.
Get the white paper
Netskope One is a cloud-native platform that offers converged security and networking services to enable your SASE and zero trust transformation.
Learn about Netskope One
Netskope NewEdge is the world’s largest, highest-performing security private cloud and provides customers with unparalleled service coverage, performance and resilience.
Learn about NewEdge
The Netskope Cloud Exchange (CE) provides customers with powerful integration tools to leverage investments across their security posture.
Learn about Cloud Exchange
- Security Service Edge Products
Protect against advanced and cloud-enabled threats and safeguard data across all vectors.
- Borderless SD-WAN
Confidently provide secure, high-performance access to every remote user, device, site, and cloud.
- Secure Access Service Edge
Netskope One SASE provides a cloud-native, fully-converged and single-vendor SASE solution.
- Security Service Edge (SSE)
- Next Gen Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- ZTNA Next
- SkopeAI
- Public Cloud Security
- Advanced Analytics
- Cloud Firewall
- Data Loss Prevention (DLP)
- Proactive Digital Experience Management
- Device Intelligence
- Remote Browser Isolation
- SaaS Security Posture Management
Intelligent Security Service Edge (SSE), Cloud Access Security Broker (CASB), Cloud Firewall, Next Generation Secure Web Gateway (SWG), and Private Access for ZTNA built natively into a single solution to help every business on its journey to Secure Access Service Edge (SASE) architecture.
Go to Products Overview
Netskope Next Gen SASE Branch converges Context-Aware SASE Fabric, Zero-Trust Hybrid Security, and SkopeAI-powered Cloud Orchestrator into a unified cloud offering, ushering in a fully modernized branch experience for the borderless enterprise.
Learn about Next Gen SASE Branch
Get your complimentary copy of the only guide to SASE design you’ll ever need.
Get the eBook
- Network Transformation
Achieve agility and efficiency through digital transformation.
- Security modernization
Meet the security challenges of today and tomorrow.
- Frameworks
Embrace the regulatory frameworks shaping cybersecurity.
- Government and Industries
Netskope helps the largest agencies and enterprises in the world secure their journey to the cloud.


Choose Netskope GovCloud to accelerate your agency’s transformation.
Learn about Netskope GovCloud
- Resources
Learn more about how Netskope can help you secure your journey to the cloud.
- Blog
Learn how Netskope enables security and networking transformation through security service edge (SSE)
- Events and Workshops
Stay ahead of the latest security trends and connect with your peers.
- Security Defined
Everything you need to know in our cybersecurity encyclopedia.
- Security Defined overview
- What is SASE?
- What is Security Service Edge?
- What is a Cloud Access Security Broker (CASB)?
- What is Zero Trust Security?
- What is a Next Generation Secure Web Gateway (SWG)?
- What is Data Loss Prevention (DLP)?
- What is SD-WAN?
- What is Generative AI?
- What is Remote Browser Isolation (RBI)?
- What is SSPM?
- What is FedRamp?
How to Use a Magic Quadrant and Other Industry Research
In this episode Max Havey, Steve Riley and Mona Faulkner dissect the intricate process of creating a Magic Quadrant and why it's much more than just a chart.

Read how Netskope can enable the Zero Trust and SASE journey through security service edge (SSE) capabilities.
Read the blog
Replay sessions from the fourth annual SASE Week.
Explore sessions
Explore the security side of SASE, the future of network and protection in the cloud.
Learn about Security Service Edge
- Company
We help you stay ahead of cloud, data, and network security challenges.
- Leadership
Our leadership team is fiercely committed to doing everything it takes to make our customers successful.
- Customer Solutions
We are here for you and with you every step of the way, ensuring your success with Netskope.
- Training and Certification
Netskope training will help you become a cloud security expert.
Netskope is proud to participate in Vision 2045: an initiative aimed to raise awareness on private industry’s role in sustainability.
Find out more












)