Hosting phishing pages or malicious payloads on legitimate cloud services is now a consolidated modus operandi for bad actors. Not only is 68% of malware delivered from the cloud, according to statistics in our July 2021 Cloud and Threat Report, but the data that we collect on a monthly basis in our Threat Labs Report tells us that Google Drive and Microsoft OneDrive steadily occupy the first two positions in the list of the cloud apps abused to deliver the most malicious content, including phishing baits and malware. Cybercriminals continue to capitalize on the growing adoption of cloud services and on the distributed workforce’s implicit trust in them.
With this in mind, it’s absolutely no surprise that new services are joining the unwelcome list of those exploited to launch malicious campaigns. In the latest example, Atlassian Confluence has been abused, for the first time, to host a phishing campaign. The attack scenario is quite simple: victims receive an email that allegedly carries a link to a confidential RFP document (yes, there is always a sense of urgency). In reality, the link points to a bait document hosted on Atlassian Confluence that redirects users to a phishing page where they need to enter their Office 365 credentials to see the RFP document. Entering these credentials of course compromises the cloud account. A variation of the same attack redirects the victim to another Atlassian Confluence page where they need to enter their Atlassian credentials (delivering them directly into the criminals’ hands).
While the service being exploited here is new, this campaign leverages old tricks: a legitimate and trusted cloud service, a familiar environment for the user, and a certain sense of urgency. From the attackers’ perspective, the exploitation of such a service allows them to easily set up the necessary infrastructure without having to take care of error-prone operational tasks, and while evading legacy web security technologies (which do not recognize the malicious context of the connection) and, as an additional bonus, evading the email security technologies that consider the link to the Atlassian Confluence page embedded in the phishing email to be legitimate.
How Netskope mitigates the risk of cloud phishing on Atlassian Confluence (and multiple additional cloud services)
Atlassian Confluence is just one of the thousands of cloud services for which the Netskope Next Gen SWG can enforce granular access control, DLP, and threat protection. If Atlassian Confluence is not part of the corporate perimeter, Netskope can block access to the entire service, or just block potentially dangerous activities (such as “Download” or “Post”). The real problem is when the organization genuinely uses Atlassian Confluence, so it cannot afford to block it completely or partially. But in this case the Netskope Next Gen SWG can go further than any other secure web gateway, being able to apply instance-based policies to Confluence and dozens more applications (for instance, differentiating “corporate Confluence” vs. “non-corporate Confluence”). As an example, the following policies allow specific activities on a Confluence instance defined as “AcmeCorp” (“Allow Corporate Confluence”), while blocking potentially dangerous activities on any other generic non-corporate Confluence (“Block any activity except View and View All or any other Confluence”).
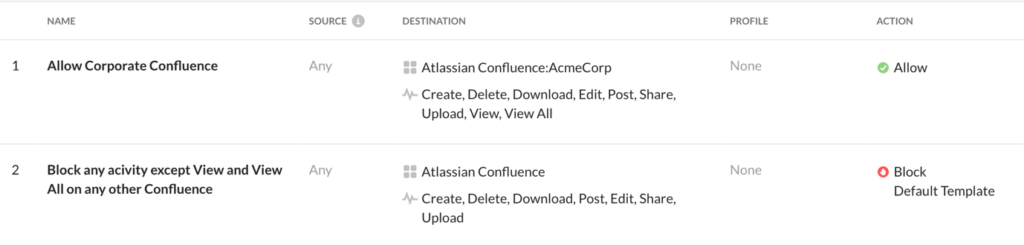
The above policies can be combined with the multi-layer threat protection engine which can scan every download (from Confluence and thousands of cloud services) and prevent any attempt to deliver malware onto the victim’s endpoint. Similarly, the DLP engine can prevent the submission of corporate credentials into phishing pages hosted on both a legitimate cloud service and a traditional domain.
Stay safe!




 Back
Back
















 ブログを読む
ブログを読む