Change is the only constant and this is especially apparent for the firewall space, as we’ve seen with branch office transformation and users continuing to work remotely. Secure Access Service Edge (SASE) architecture, when properly designed, puts the user in the center with cloud edge security services protecting them, their data, and the apps and websites they use every day, on either company or personal instances. To keep users productive, branch offices need network security for all outbound ports and protocols without having to hairpin traffic from their remote workers back to the main data center enterprise firewall, which results in a poor user experience.
Firewall-as-a-Service (FWaaS) offerings provide cloud firewall services to users and offices for outbound egress traffic. The most recent Gartner Enterprise Firewall Magic Quadrant, in November 2020, showed only four of 17 vendors listed as having FWaaS solutions available, with a fifth vendor recently announcing their new cloud firewall in 2021. But FWaaS adoption is growing rapidly; Gartner further notes that by 2025, 30% of new distributed branch office firewall deployments will switch to Firewall-as-a-Service, up from less than 5% in 2020.
While the pandemic resulted in increased spending on VPN solutions at first, the longer-term strategy shows increasing FWaaS to support working from anywhere, increasing cloud adoption favoring cloud security solutions, a movement to zero trust in parallel with FWaaS interest, and cost optimization driving consolidation with fewer branch offices. FWaaS is projected to be one of the fastest-growing and top three revenue-driving components of SASE architecture next to secure web gateway (SWG) and cloud access security broker (CASB).
Understanding these new cloud firewalls requires some careful reading between the lines, because some products marketed as “FWaaS” may in fact leverage a legacy VPN path to a cloud-hosted firewall image, and then utilize more service chains to other defenses resulting in multiple hops, increased latency, and a poor user experience. Integration into one platform, one console, and one policy engine makes a big difference if you desire less complexity, more consolidation, and lower total cost of operations. When evaluating FWaaS, avoid checklists and multiple consoles, and always test for desired performance and user experience.
The Netskope Cloud Firewall (CFW), announced today as part of a number of key enhancements to the Netskope Security Cloud, is fully integrated into our SASE architecture with network security for users and offices for all outbound ports and protocols for TCP, UDP, and ICMP. Beyond the expected 5-tuple firewall policy egress controls is support for users and groups, FQDNs and wildcards, an application layer gateway for FTP, and firewall event logging. More importantly, on the same cloud security platform, your web and cloud traffic are inspected by the Netskope Next Gen SWG with threat and data protection defenses running on NewEdge, the world’s largest and highest performing private network cloud.
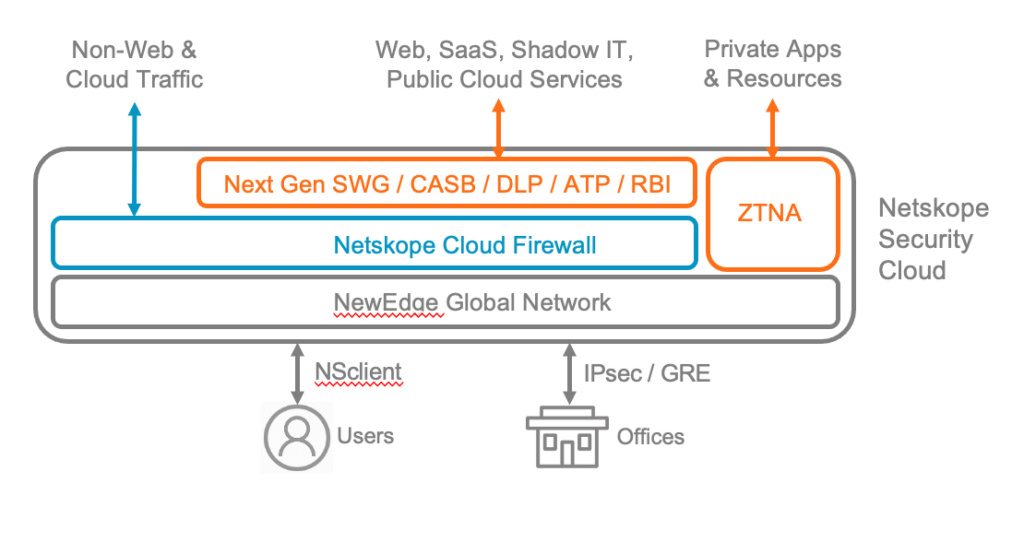
Netskope CFW is available to users and offices across the globe with centralized management and without the hardware or firmware update headaches or reliance on endpoint firewall agents. NewEdge provides a fast user experience with security across network egress protocols and ports all the way to the company or personal app instances that can otherwise lead to cloud malware delivery, phishing attacks, or data exfiltration. The Netskope Security Cloud has SASE integration with security from Layer 3 to the apps and data that drive your organization’s success.
To learn more about the Netskope Cloud Firewall, please visit our product web page and watch the demonstration video.
Join Netskope for “Unpacking updates to the Netskope SASE and Zero Trust Platform” on September 16, 2021, when you’ll learn where Netskope fits into the SASE architecture, an overview of the new and updated Netskope products, and how the benefits of these products mean better security, faster performance, and lower total cost of ownership.




 Back
Back
















 ブログを読む
ブログを読む