Summary
Just a few days after CVE-2021-45046 was released and fixed, a third zero-day vulnerability was discovered in Apache Log4j, tracked as CVE-2021-45105. The bug was reported on December 15, 2021, and disclosed on December 18, 2021.
This third vulnerability has received a CVSS score of 7.5 out of 10, whereas the first one known as Log4Shell (CVE-2021-44228) received the maximum CVSS score of 10 due to its criticality. The second vulnerability (CVE-2021-45046) had received a CVSS score of 3.7 initially but was later changed to 9.0, as it could also allow Remote Code Execution attacks.
This security issue affects Apache Log4j versions 2.0-beta9 to 2.16.0 and could allow attackers with control over the Thread Context Map (MDC) input data to perform a DoS attack. Although this bug lies in the same library, it’s not a variant from Log4Shell, as it can also abuse non-JNDI lookups.
CVE-2021-45105
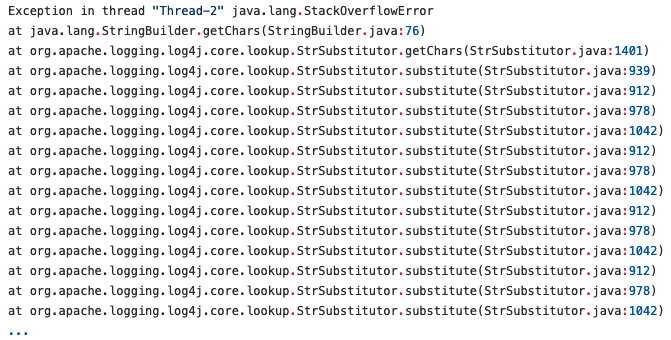
An attacker with input control (e.g. through the Thread Context Map) can create a malicious lookup variable that will cause an infinite recursive lookup, resulting in a process crash and DoS (Denial of Service).

This is possible because when a nested variable is replaced by the “StrSubstitutor” class, the “substitute()” method is called recursively. Therefore, if the nested variable references the variable itself, the substitution flow causes an infinite recursion that results in a process crash.
For example, given the following Pattern Layout with the Context Lookup of “${ctx.loginId}”, if we assign the value as “${${ctx:loginId}}”, the code will be recursively substituted in an infinite loop.
A complete analysis of the vulnerability was released by the Zero Day Initiative.
Conclusion
Organizations have likely already upgraded Log4j twice in the past 10 days and should upgrade Log4j again to address this new vulnerability. Attackers have been exploiting the first two Log4j vulnerabilities since they were disclosed and will soon start exploiting this latest vulnerability.
Protection
Netskope Threat Labs is actively monitoring this campaign and will ensure coverage for all known threat indicators and payloads.
Update/Patch
CVE-2021-45105 was fixed in Log4j 2.17.0, we strongly recommend everyone to update Apache Log4j to this latest version. This issue can also be mitigated by changing your logging configuration to either replace Context Lookups like ${ctx:loginId} or $${ctx:loginId} with Thread Context Map patterns (%X, %mdc, or %MDC), or by removing references to Context Lookups like ${ctx:loginId} or $${ctx:loginId} where they are sourced from external inputs, such as HTTP headers or other user inputs.
Netskope Private Access
If you are running internal applications that cannot be immediately patched, you can mitigate the risk of exploitation by limiting access to the app. A private access solution, such as Netskope Private Access, can be used to make private apps invisible to external attackers who seek to exploit vulnerable services. Furthermore, a private access solution can restrict access to a private app internally, such that only authorized users are able to access the app, reducing the risk that a compromised user or device could be used to exploit vulnerable services.




 Back
Back 















 Read the blog
Read the blog