Internet-connected devices (also known as “the internet of things”) are a key business enabler for modern enterprises focused on transforming their businesses and gaining competitive advantage through automation and intelligent decision-making. According to IDC, there will be over 55.7 billion connected IoT devices (or “things”) by 2025, generating almost 80B zettabytes (ZB) of data.
While this underlines the enormous opportunity presented by IoT, the effective security for connected devices hasn’t kept pace with their increasing adoption. While more than 1.5 billion IoT breaches occurred in the first half of 2021, a remarkable 136% increase from the previous six months, the breaches are expected to increase in the coming years with the growth in total number of deployed IoT devices.
During the pandemic, many IoT and IT devices were left behind in corporate environments when employees transitioned to remote work. Management oversight and lack of security updates have made these devices highly susceptible to targeted cyberattacks. With hybrid work now normal, employees are expected to bring a diverse set of corporate and personal devices for use in their jobs. The Netskope Device Intelligence engineering team collected and analyzed the number of connected devices at a representative customer site within a fixed time period in 2021 (“Before”) and 2022 (“Now”). As evident from the graphs below, there has been a huge surge in the number of unmanaged devices within the representative customer site in 2022, as compared to 2021. These devices will further interact with the IoT devices in the corporate networks, creating a significantly larger attack surface to manage and control.
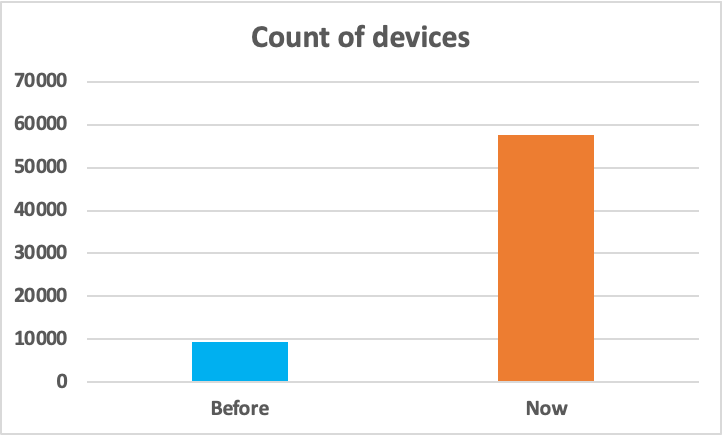
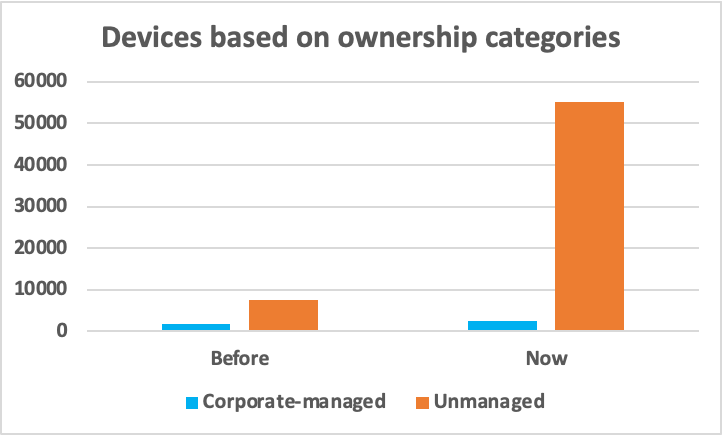
Threat actors keep finding new ways to infiltrate connected devices every day, and the trend will continue to accelerate as IoT solidifies its presence in mainstream business use.
The way forward
To better secure hybrid enterprises, it is critical to account for every device connected to the corporate network, understand their behavior and dynamic risk posture, and ensure they have the right permissions for accessing internal resources or carrying out their specific business functions. In this regard, here are some of our recommendations for mitigating IoT-related risks:
Establish a baseline
Establish a baseline of network and IoT devices before employees return to offices. Identify the normal behavioral pattern of connecting devices and audit the devices that exhibit anomalous behavior, such as devices connecting for extended periods or beyond normal working hours.
Discover all the connected devices
Account for both managed and unmanaged devices in the corporate environments. Automated discovery of every device connecting to the corporate environment has become increasingly important in the current hybrid work landscape where nearly half of the devices on enterprise networks are unmanaged and IoT and companies are adopting flexible policies to allow internal data access from non-corporate managed devices to ensure business continuity.
Understand the context
Generate rich and dynamic context around every connected device by collecting device information across multiple dimensions—physical, logical, operational, and locational touch points. With the right solution, this contextual information can be combined with machine learning algorithms to generate distinctive models and signatures for each device, allowing for accurate policy control and minimizing the organization’s exposure to potential device-level risks.
Perform continuous risk assessment
The risk posture of a connected device is a factor of multiple attributes, including device type, usage, behavior, owner, location, time of the day, OS updates, and many more. Continuously monitor the connected devices for anomalies and unauthorized access, and enforce security policies that take into account the dynamic risk scores of devices based on their real-time behavior.
Microsegment the networks
Group similar devices within secure zones or software-defined perimeters for tighter visibility and governance over each activity in the coporate environment. Microsegmentation also completely isolates risky devices from the broader IT infrastructure, providing a stronger regulatory compliance posture and preventing lateral movement of threats to reduce the overall attack surface.
Enforce policies at scale
Utilize the rich contextual information and micro-segmentation capabilities to tailor security and create dynamic access control policies at scale based on multiple contextual factors such as device type, interface, and functionality; logical properties such as ownership and control; threat and risk assessment; and dynamic properties such as location and time. For example, applying network access control rules for grouping all smart cameras and blocking their access from unmanaged devices.
How Netskope Device Intelligence addresses the device security gaps in the hybrid enterprise
Netskope Device Intelligence is an agentless, innovative, and smart device security solution that provides visibility into all the internet-connected “Things” in the enterprise network and secures them with a context-driven, zero trust approach. The solution’s HyperContext® platform uncovers managed and unmanaged devices on both the radio and network spectrum and leverages AI/ML algorithms to generate deep, device-level contextual intelligence for solving the hybrid enterprise challenges through the following use cases:
- Device classification and visibility: Scanning the hybrid enterprise landscape to discover and classify a range of managed, unmanaged, and IoT devices, including smartphones, audio conferencing devices, smart cameras, thermostats, etc., with rich contextual information for deep insights into device behavior and activity.
- Cybersecurity asset management: Comprehensive asset management with built-in asset inventory engine. The solution correlates multiple device interfaces to a single entity, providing an accurate account of devices and driving mandatory service compliance in adherence to corporate policies.
- Device risk: Continuous monitoring of devices to detect anomalies and generate unique device risk scores based on their characteristics and activities, exchanging device attributes with SIEM and SOAR tools for automated remedial actions and minimizing alert fatigue.
- Access control and segmentation: Dynamic asset grouping and micro segmentation based on context and real-time device behavior, and orchestrating actions using existing network systems such as network access control (NAC), firewalls, and access points.




 戻る
戻る
















 ブログを読む
ブログを読む