Last week, security researchers revealed several high-severity vulnerabilities related to Stagefright, a native Android media player library. The vulnerabilities leave close to a billion devices open to remote code execution. Attackers can exploit the vulnerabilities by sending a specially designed media file via multimedia messaging service (MMS) or another channel to a victim’s mobile device. Victims may not even have to open the message to be vulnerable, and in some cases victims can become vulnerable by visiting a Web page hosting the malicious file or accessing the file via a separate Android application.
What does this mean for end users and enterprises? Here are some immediate recommendations:
End users should disable the “auto-retrieve” function from their MMS settings. A quick and easy-to-follow guide can be found here. A patch has been released, but it may take a while for the patch to reach the billion vulnerable devices, as device manufacturers have to now release patches for each type of device. Therefore, until you are confident that your device has been patched, the device remains vulnerable and can be compromised if a malformed media file is downloaded.
Enterprises that use a Cloud Access Security Broker (CASB) such as Netskope can follow these relatively quick steps to protect sensitive data from exploitation:
- Report: Discover who the Android users accessing corporate cloud apps in your organization are:
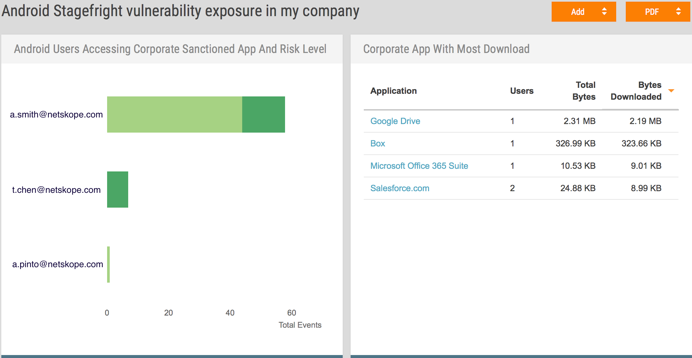
- Downgrade access: Prevent those users from certain activities such as editing, downloading, sharing, and deleting certain types of sensitive data, but still allow them to preview those documents online.
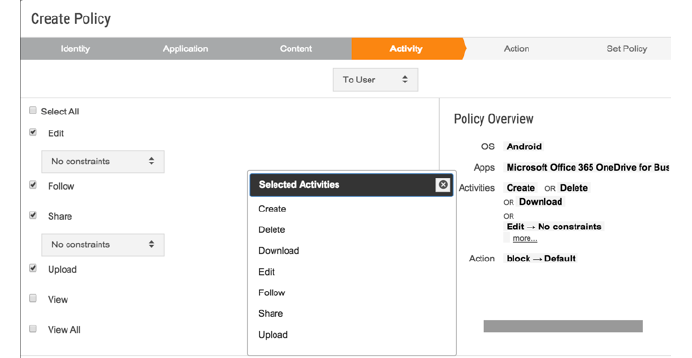
- Alert: Be informed of any suspicious activities and use machine-learning techniques to prevent future exploits. Alerts can also be streamed to an external SIEM tool for further measures.
Instead of blocking access to cloud apps entirely (which will frustrate users and severely impact productivity), with Netskope enterprises can block risky activities while still allowing the activities that need to happen. This surgical visibility and control of the cloud apps in an organization and contextual data protection enables enterprises to enforce security without getting in the way of business.




 Back
Back















 ブログを読む
ブログを読む