Summary
In October 2022, a novel ransomware named Prestige was found targeting logistics and transportation sectors in Ukraine and Poland. According to Microsoft, victims affected by Prestige overlap with previous victims targeted by HermeticWiper, spotted in February 2022.
The research also shows that the attackers deployed the ransomware within an hour between all victims, abusing highly privileged domain credentials to deploy the payload. Prestige also appeared among the top five ransomware families blocked by Netskope in October 2022.
In November 2022, a new research linked Prestige ransomware with a Russian-based threat actor known as IRIDIUM, which overlaps with Sandworm, another threat group that is linked to destructive attacks since the war started in Ukraine. In this blog post, we will show how Prestige ransomware works.
Analysis
The sample we analyzed was likely compiled on October 7, 2022 and it’s written in C/C++.
Once executed, Prestige creates its ransom note named “README” in the “C:\Users\Public” folder. The note is also created in folders where there are files encrypted by this ransomware.
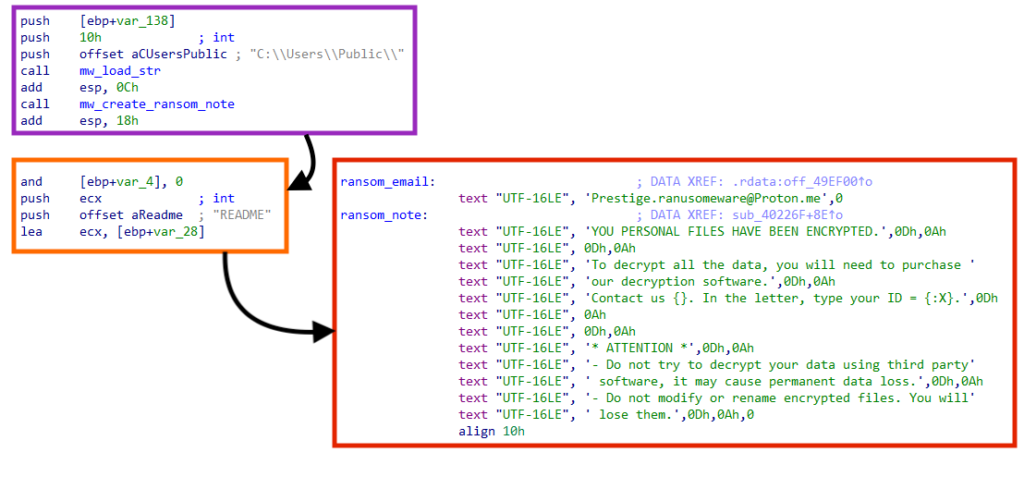
Prestige then modifies the Windows registry to make notepad open the ransom note every time an “.enc” file is opened, using the following commands:
- C:\Windows\System32\reg.exe add HKCR\.enc /ve /t REG_SZ /d enc /f
- C:\Windows\System32\reg.exe add HKCR\enc\shell\open\command /ve /t REG_SZ /d \”C:\Windows\Notepad.exe C:\Users\Public\README\” /f
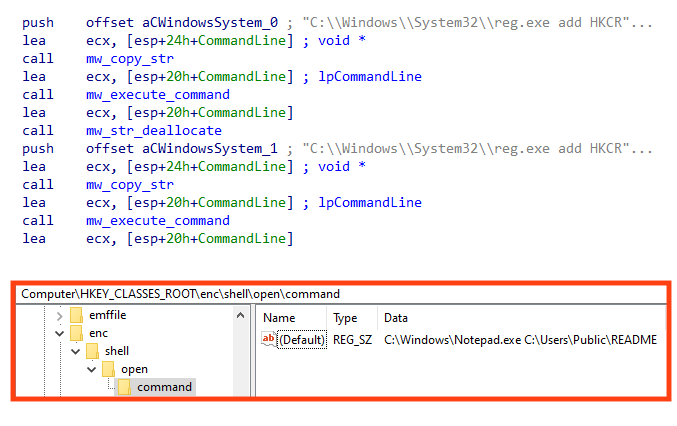
Prestige tries to stop the MSSQL Windows service to avoid issues during the encryption of the files, by running the following command:
- C:\Windows\System32\net.exe stop MSSQLSERVER
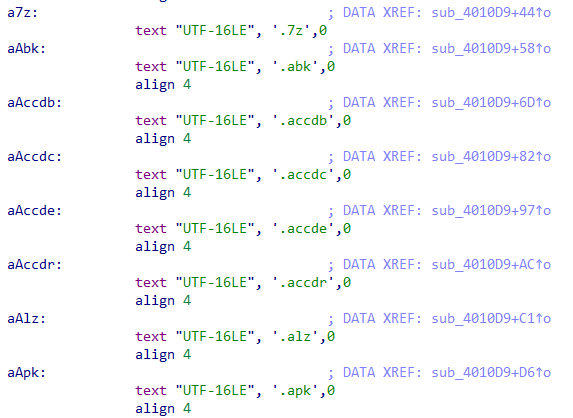
Then, the ransomware starts the encryption process by searching files with specific extensions, which can be found below.
.1cd, .7z, .abk, .accdb, .accdc, .accde, .accdr, .alz, .apk, .apng, .arc, .asd, .asf, .asm, .asx, .avhd, .avi, .avif, .bac, .backup, .bak, .bak2, .bak3, .bh, .bkp, .bkup, .bkz, .bmp, .btr, .bz, .bz2, .bzip, .bzip2, .c, .cab, .cer, .cf, .cfu, .cpp, .crt, .css, .db, .db-wal, .db3, .dbf, .der, .dmg, .dmp, .doc, .docm, .docx, .dot, .dotm, .dotx, .dpx, .dsk, .dt, .dump, .dz, .ecf, .edb, .epf, .exb, .ged, .gif, .gpg, .gzi, .gzip, .hdd, .img, .iso, .jar, .java, .jpeg, .jpg, .js, .json, .kdb, .key, .lz, .lz4, .lzh, .lzma, .mdmr, .mkv, .mov, .mp3, .mp4, .mpeg, .myd, .nude, .nvram, .oab, .odf, .ods, .old, .ott, .ovf, .p12, .pac, .pdf, .pem, .pfl, .pfx, .php, .pkg, .png, .pot, .potm, .potx, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prf, .pvm, .py, .qcow, .qcow2, .r0, .rar, .raw, .rz, .s7z, .sdb, .sdc, .sdd, .sdf, .sfx, .skey, .sldm, .sldx, .sql, .sqlite, .svd, .svg, .tar, .taz, .tbz, .tbz2, .tg, .tib, .tiff, .trn, .txt, .txz, .tz, .vb, .vbox, .vbox-old, .vbox-prev, .vdi, .vdx, .vhd, .vhdx, .vmc, .vmdk, .vmem, .vmsd, .vmsn, .vmss, .vmx, .vmxf, .vsd, .vsdx, .vss, .vst, .vsx, .vtx, .wav, .wbk, .webp, .wmdb, .wmv, .xar, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xz, .z, .zbf, .zip, .zipx, .zl, .zpi, .zz
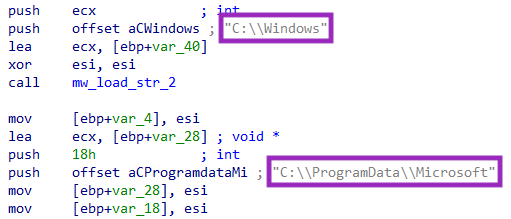
This ransomware skips the encryption process in the folders “C:\Windows” and “C:\ProgramData\Microsoft“.
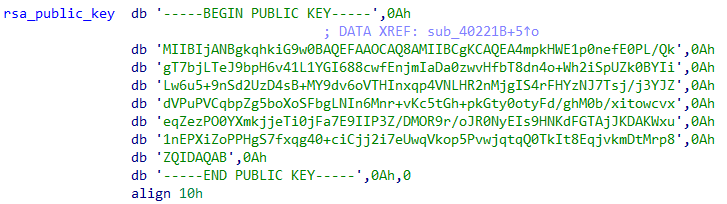
Prestige encrypts the files with AES using the Crypto++ library. The malware then uses RSA to protect the key, which is a common behavior among ransomware.
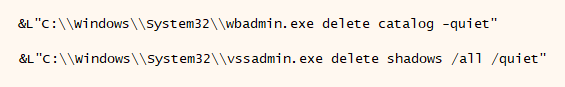
Furthermore, Prestige abuses both wbadmin and vssadmin utilities to delete backup and volume shadow copies on the system, using the following commands:
- C:\Windows\System32\wbadmin.exe delete catalog -quiet
- C:\Windows\System32\vssadmin.exe delete shadows /all /quiet
As previously mentioned, Prestige adds the “.enc” extension to encrypted files. If the victim tries to open any of these files, then the ransom note is displayed via Notepad.
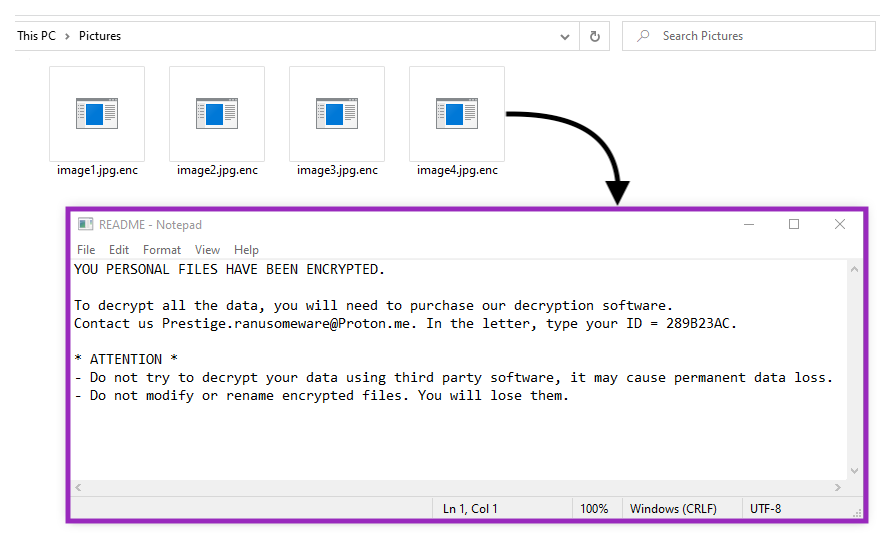
Unlike other ransomware groups, like BlackCat or LockBit, Prestige doesn’t provide a website hosted on the deep web as a contact point. Instead, they ask the victim to send an email to a Proton address, along with an ID for identification.
Conclusion
As the war in Ukraine continues to develop, we should expect more threats like the Prestige ransomware targeting Ukrainian citizens and allies. Because the attackers behind this threat were found to be abusing highly privileged credentials, we strongly recommend organizations to revisit password policies and enable MFA to mitigate abuse in compromised accounts.
Furthermore, ransomware groups often use Living-off-the-Land techniques to carry out attacks, such as abusing PsExec or WMI. Thus, we recommend blocking process creation sourced from these tools, as well as using tools like SIGMA to monitor possible Living-off-the-Land abuse. Using a secure web gateway is also strongly recommended to be able to identify and block web traffic related to threats like Prestige in real time.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Threat Protection
- Win32.Ransomware.Prestige
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Malware.Detect.By.Sandbox indicates a sample that was detected by our cloud sandbox
IOCs
All the IOCs related to this campaign and a Yara rule can be found in our GitHub repository.




 戻る
戻る
















 ブログを読む
ブログを読む