Unfortunately, we have already seen ransomware auto-propagate in the form of the Virlock file infector, now we have the Wana Crypt0r 2.0 worm fully automated. The significance of this is that the victim is entirely passive in the infection. Simply being unpatched could lead to an infection causing the victim’s files to become encrypted. The Wana Crypt0r ransomware worm was created by mating the Equation Group’s ETERNALBLUE exploit for MS17-010 with the previous generation of the ransomware. Wana Crypt0r ransomware is also known as Wana Decrypt0r 2.0, WannaCry, WCry, and WanaCrypt. Upon infection, it makes recovery more difficult by deleting the Volume Shadow copies and backups.
Because ransomware like Wana Crypt0r 2.0 is able to delete Volume Shadow copies, Netskope advises users to backup important files in the cloud and to turn on versioning. This will create a recoverable backup solution that is difficult for ransomware authors to defeat. Netskope also detects copies of the Wana Crypt0r 2.0 executable as Backdoor.WannaCryptr.A, Backdoor.Wannacryptr.B, Backdoor.Wannacryptr.C or Backdoor.Wannacryptr.D.
Upon execution, encrypted files will be renamed to use extensions such as .wncry, .wnry, .wcry and .wncrypt. The following ransom note will be displayed, which provides a test mechanism to decrypt some files for free.
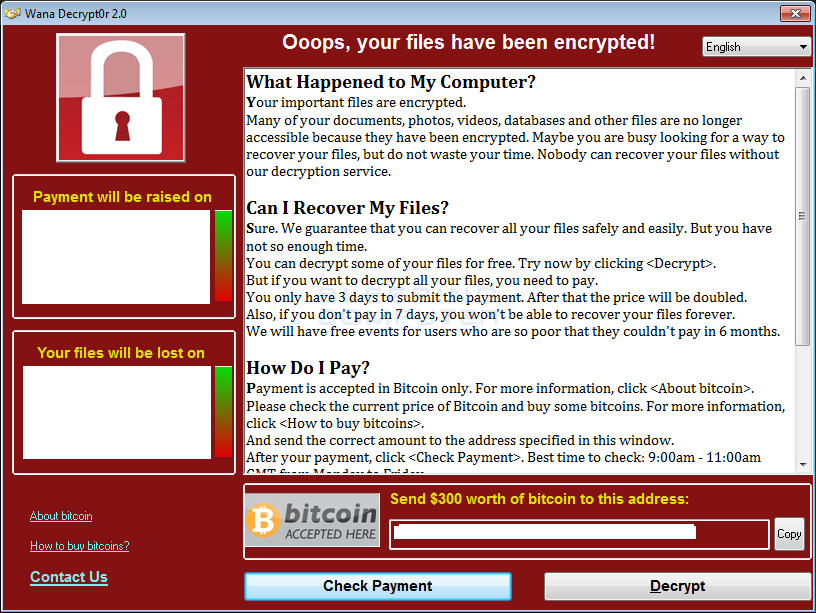 Figure 1: Ransom note from WannaCryptr
Figure 1: Ransom note from WannaCryptr
General Recommendations
Netskope recommends the following best practices to enterprises in order to protect from ransomware threats:
- Detect and remediate all threats at rest in sanctioned cloud services using a threat-aware cloud access security broker (CASB) like Netskope.
- Detect and remediate all threats being downloaded from unsanctioned cloud services using a threat-aware cloud access security broker (CASB) like Netskope.
- Regularly back up and turn on versioning for critical content in cloud services.
- On managed devices, administrators should enable the option to view known file extensions.
- Administrators should advise their users to avoid executing any files with dual extensions unless they are very sure that the files are benign.
- Administrators should warn users to avoid opening untrusted attachments, regardless of those attachments’ extensions or file names
- Enterprise users should always keep their systems and antivirus updated with the latest releases and patches. Microsoft has released the following Security Update for MS17-010.
Security Update for Microsoft Windows SMB Server (4013389)
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- Disable SMB for the functions not using it within an enterprise. Additional details can be found in the following Microsoft support article.
How to enable and disable SMBv1, SMBv2, and SMBv3 in Windows and Windows Server
https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
- Administrators can also consider adding rules to specific firewall ports to prevent SMB traffic from leaving the corporate environment as mentioned in the following Microsoft article
https://support.microsoft.com/en-in/help/3185535/guidelines-for-blocking-specific-firewall-ports-to-prevent-smb-traffic-from-leaving-the-corporate-environment




 Back
Back















 Read the blog
Read the blog