Have you recently moved PCI cardholder data to Amazon Web Services (AWS)? AWS has been PCI DSS certified for many years but you still need to take steps to ensure your payment card data is “secure in the cloud.” Ultimately, the responsibility for PCI compliance rests on you, not AWS.
Why is PCI DSS compliance important?
It is important to be PCI DSS compliant as companies are increasingly relying on technology to gather cardholder information. When you are PCI DSS compliant, this can help assure your customers that their information is protected.
How does AWS PCI compliance work?
Although AWS is PCI compliant, it does use a shared responsibility model. This means that if you have moved your PCI cardholder data into AWS, you share the responsibility for PCI compliance. However, because AWS is PCI-compliant, if you choose to use AWS, you do not need to worry about assessing AWS infrastructure for PCI compliance. Also, because AWS is PCI DSS compliant, if you have chosen to use AWS with your PCI cardholder data, you can rely on AWS to both get and manage your PCI certification.
How does the AWS Virtual Private Cloud (VPC) help protect data?
The AWS VPC allows a company to create and use a private network for storing cardholder data. Using the AWS VPC is a great way to segment your data by securing it separately, thus adding additional protection to the data.
This additional protection includes Secure Sockets Layer (SSL) and Transport Layer Security (TLS) to help protect data. These layers help verify that a website is secure. When you visit a website, your computer’s browser requests a certificate to verify that the website you are attempting to access isn’t malware/ransomware. The website will then send a certificate back to your computer using TLS/SSL to verify that it is secure. However, this exchange of information can often slow down information transmission, which can bother customers. But, elastic load balancing (ELP) can help to speed things up.
ELP in AWC VPS helps to protect data by spreading out requests across different servers. This helps to speed up the process of transmitting information, while helping the data to be more secure as this process adds additional encryption layers.
What are the PCI DSS requirements?
Although there are 12 requirements you must follow to be PCI DSS complaint, they can be simplified to the following six areas:
- Ensure you have a Secure Network: Use a firewall to protect your data, but don’t use the security protocols from the firewall vendor.
- Protect your Data: Protect sensitive cardholder data through encryption in public networks.
- Ensure Access Control: Restrict access to cardholder data by making sure users verify their identity before they are granted access to data.
- Have a Vulnerability Management Program: You can reduce the vulnerability of your data network to malware by making sure you use antivirus programs or software.
- Create Information Security Policies: Ensure that you have a policy that documents the steps and procedures that all employees must follow when working with secure data.
- Monitor your Network: Monitor and test your network access often. Ensure to check your security system as well.
According to the 2018 Cloud Security Report from Cybersecurity Insiders, the top two security control challenges SOCs struggle with most are visibility into infrastructure security (43 percent) and compliance (38 percent). With mounting pressure from regulatory, external, and internal audits, how can you achieve both compliance and security when implementing security controls?
Netskope can tell you instantly what it would take an auditor days to figure out and communicate the information back to you in an easy to understand, visual format.
With various environments and accounts, Netskope can help highlight and remediate any compliance gaps. Netskope can help fix issues such as overly permissive security group rules and weak password policies, and enforce requirements and prove compliance in audits. Administrators can also create and enforce custom rules that describe unique restrictions and compliance practices in their organizations.
In a few easy steps, use Netskope to find out if your cloud infrastructure environment is PCI compliant:
Step 1: Grant Netskope API read-only access to the configuration settings of your cloud environment.
Netskope links to your AWS account via API access and pulls the data without any customization from the user.
Step 2: Create and run the Security Assessment policy.
From the main dashboard, select the PCI profile you want to run your assessment on for the specific accounts you want to check. Netskope security checks are mapped to PCI DSS and CIS Foundations Benchmark and will assist you in assessing your environment against these requirements.
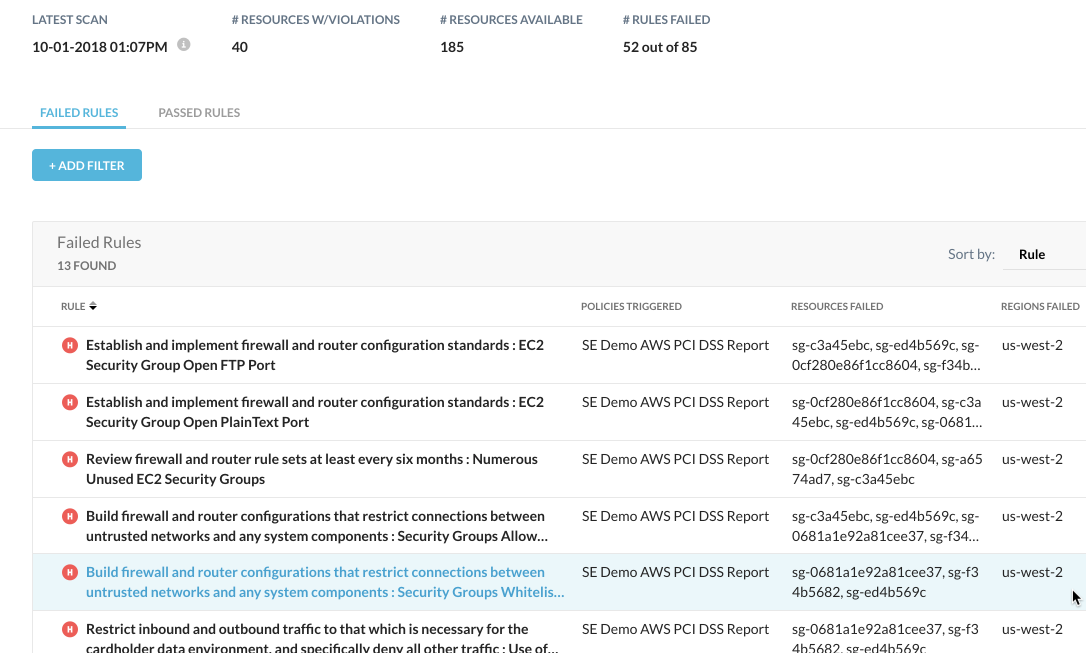
Step 3: View your report.
See a customized report with the results of your assessment that tells you if you have met compliance standards. Failed checks are listed by severity level. Further drill into each check for recommended remediation steps to get back into compliance.
Step 4: Share report results with an auditor or internal teams.
Instantly, turn the report into a PDF and send to an auditor.
Don’t waste hours combing through PCI DSS compliance standards to see if you are PCI compliant. Ensuring PCI compliance in your cloud infrastructure environment is easy with Netskope—it just takes four simple steps. Save time and resources today by letting Netskope check your PCI compliance for you. Request a demo today!




 Back
Back















 Read the blog
Read the blog