Updated 7/17/25
With AI fueling so much of what causes data security leaders to lose sleep at night, at least one thing is clear: data security posture management (DSPM) and data loss prevention (DLP) are no longer optional. Instead, they are complementary essentials for a modern, risk-aware data security strategy that simplifies compliance and ensures protection against ever-evolving threats while safely enabling innovation and performance without tradeoffs.
So, if you’ve been treating DSPM and DLP as separate silos, it’s time to rethink your data security strategy. They can work together to form the backbone of a comprehensive approach that not only protects your data, but also positions your organization to be a trusted partner in today’s data-driven economy where AI is touching almost every application, every online location, and every data user (human or not).
Why DSPM and DLP are better together
As mentioned above, DSPM and DLP aren’t just complementary, they’re interdependent. One without the other is like locking your front door while leaving the windows wide open.
DSPM is your detective for data security. It pinpoints exactly where sensitive structured and unstructured data resides in both the cloud and on premises, evaluates the associated risk, and ensures that it’s stored and accessed securely. DSPM operates at the core of your data storage environments (cloud, hybrid, and on-prem), identifying blind spots and aligning security configurations with compliance standards. DSPM is about data at rest and ensures you know where your sensitive data lives and that it’s properly secured before attackers (or auditors) come knocking.
With DSPM as the detective, DLP is the enforcer. It focuses on data in motion, protecting sensitive information as users access it in the cloud or on premises, use it, and move it across systems, including AI applications. DLP watches for risky behaviors, whether it’s an employee trying to upload confidential data to an unsanctioned app or mistakenly sharing sensitive data externally, and takes immediate action to block or prevent leaks.
Together, DSPM and DLP secure the full lifecycle of your data: where it lives, how it’s accessed, where it’s going, and always with protection from AI risks in mind.
With those functions in mind, let’s take a closer look at why they work better when part of a unified data security approach:
1. DSPM lays the foundation
DSPM is your starting point. Without knowing what sensitive data you have, where that sensitive data islives, how it’s stored, or where security vulnerabilities in potential data interactions lie, your DLP strategy is flying blind. DSPM finds and uncovers the critical areas that DLP needs to protect, ensuring your efforts are targeted and effective.
2. DLP provides immediate defense
While DSPM finds the data and maps risks, DLP delivers real-time protection. It enforces policies and intercepts threats as they occur, whether intentional or accidental. DLP takes the insights DSPM provides and acts on them, creating a seamless line of defense.
3. Together, they cover the entire data lifecycle
Full data security isn’t just about protecting data where it lives or catching breaches in transit. It’s about both. DSPM ensures your data is secure at rest, while DLP actively monitors and protects it in motion.
This holistic approach eliminates gaps and ensures continuous protection, no matter how or where your data flows.
Unifying DSPM and DLP: Teamwork makes the data security dream work
Now that we understand how the detective capabilities of DSPM and the enforcement powers of DLP are interdependent, we get a clear picture of why they need to work together seamlessly. When unified, DSPM and DLP become a powerful data security solution that provides complete visibility, real-time protection, and ongoing compliance and security posture management.
Visibility and discovery (DSPM)
DSPM acts as the lens through which you gain full visibility into your sensitive data. It classifies information in structured and unstructured formats, creating a roadmap for where risks exist. This visibility is what makes DLP more strategic and intelligent, focusing on high-value data instead of wasting resources on noise.
Real-time enforcement (DLP)
DLP takes DSPM’s insights and applies precision protection in real-time. When it is unified with DSPM, organizations can ensure DLP has the necessary context to detect and respond effectively to data security risks effectively. Here are a few examples:
- If DSPM flags a critical database or AI application for having weak access or upload controls, DLP can enforce restrictions and prevent data from being exfiltrated or misused.
- Without DSPM fully paired with DLP when it comes to preventing lateral movement, an attacker attempting steal data could more easily slip by.
- Real-time data masking also becomes seamless, as DSPM’s insights inform exactly what needs protection, all so incidents like exfiltration through an AI application are minimized through swift containment.ent.
Enhanced incident response with exact data matching
With DSPM providing granular visibility into your organization’s sensitive data at rest, DLP can leverage this intelligence to enable enhanced incident response capabilities. By creating a comprehensive profile of your critical assets and their associated risks, you can inform the detection engine to identify specific data patterns, anomalies, or indicators of compromise (IOCs). This allows for direct correlation of exact matches between data in motion and data at rest, reducing false positives and ensuring timely and effective incident response.
The key idea here is that by connecting DSPM’s insights on data at rest with DLP’s detection capabilities, organizations can achieve more accurate and effective threat detection. By matching actual data in transit against a profile of sensitive assets, DLP can quickly identify high-confidence threats and initiate precise responses to mitigate damage.
Ongoing compliance and security posture
Regulatory requirements like GDPR, CCPA, or HIPAA aren’t just about checkboxes, but also about protecting trust. DSPM ensures compliance by continuously monitoring and classifying sensitive data, while DLP ensures data isn’t leaked or mishandled through uncontrolled AI usage or otherwise, reducing legal and reputational risks.
Closing gaps in your data security strategy
Data security isn’t static. It’s dynamic, evolving, and constantly being tested by adversaries, especially in this daily-changing AI era we live in. As a security leader, your challenge isn’t just to prevent breaches, it’s also to stay ahead of them. That requires tools that are unified instead of operating in isolation.
DSPM and DLP should be considered two sides of the same coin. DSPM gives you the intelligence you need to understand where your data is and what the associated usage risks are, while DLP enforces protections in real time. Without the right cohesion, you’re leaving gaps that attackers will exploit.
As you evaluate your data security strategy in today’s AI-driven world, ask yourself: Am I building a system that covers the full end-to-end data lifecycle? If not, it’s time to rethink. DSPM and DLP aren’t just better together, they’re necessary together.
Complete your unified data security strategy!
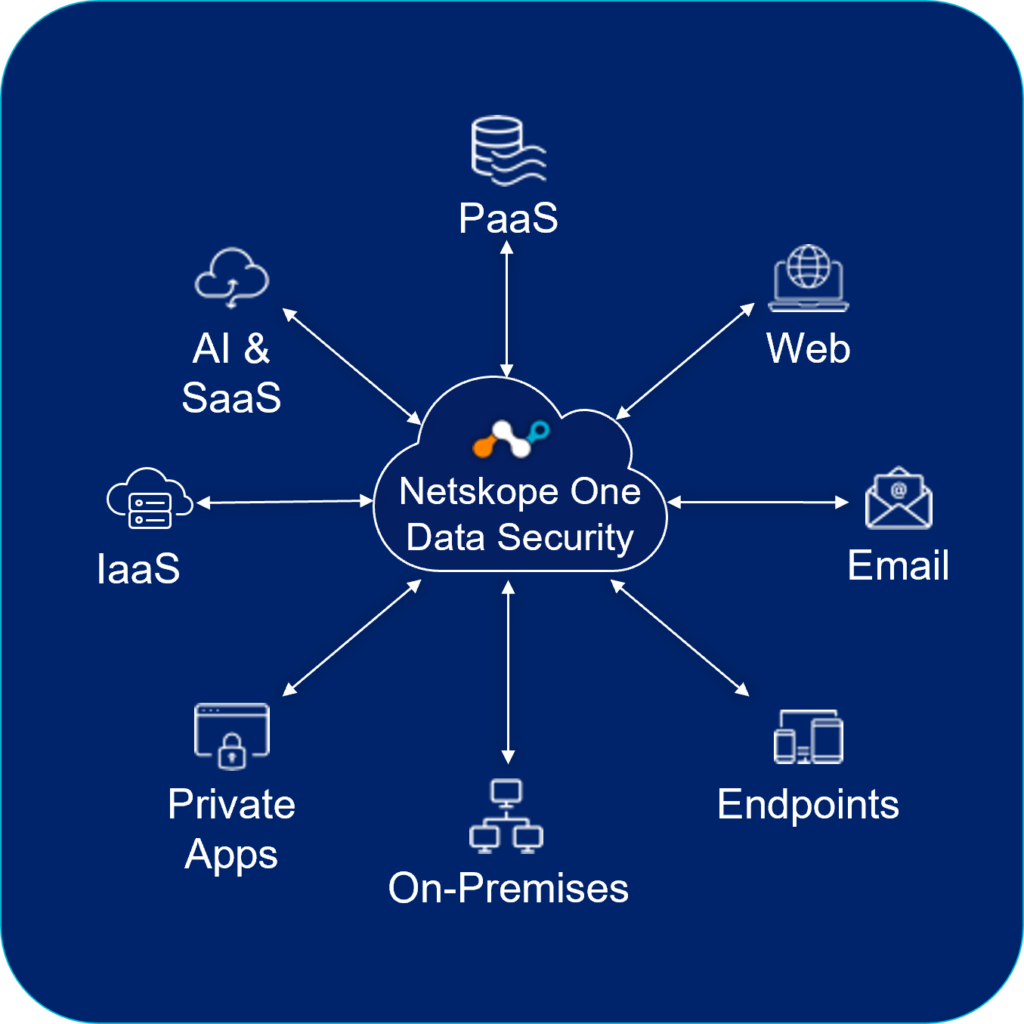
Don’t leave gaps in your defense. Learn how Netskope One Data Security unites the divide between visibility and protection, providing real-time enforcement and proactive compliance management.
But unified data security only scratches the surface of what Netskope provides. Gartner has put Netskope in its Leader category in all four of its SSE Magic Quadrants since 2022, and in both of its SASE Magic Quadrants since 2024 (Read the 2025 report!). And, not only does Netskope stand out from other SSE vendors with the best “Completeness of Vision” in the 2025 SSE MQ in particular, but it also is the only vendor ranked among the two highest scoring vendors for all six category use cases in the 2025 Gartner Critical Capabilities Report for SSE, and in all four category use cases in the 2025 Gartner Critical Capabilities Report for SASE Platforms.




 Back
Back 















 Read the blog
Read the blog