The enterprise business is now borderless, where users, devices, sites, and clouds are all creating any-to-any connections with new access control requirements. Digital innovation has led to the proliferation of apps and IoT devices where the cloud and web have become an encyclopedia of applications.
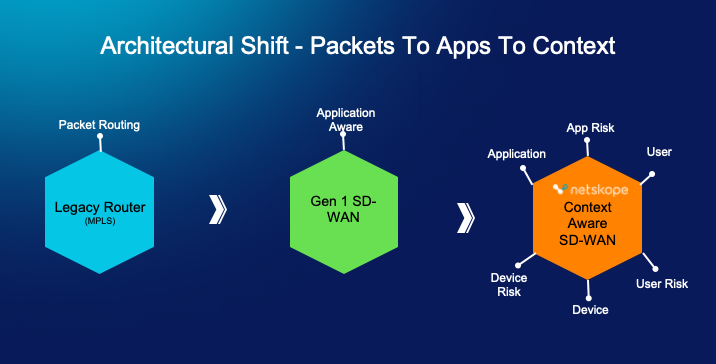
Back in the 2000s, MPLS was used to backhaul all traffic to central data centers to consume on-premise applications, which was efficient and delivered with SLAs. Then in the 2010s, the increasing demand for voice, video collaboration, and cloud applications resulted in a need for increased WAN bandwidth in the branch. MPLS became expensive, static, and lacked application level visibility and control. SD-WAN emerged to solve these challenges, combining internet economics with application visibility and control over low cost internet-transport.
Now, we’re at another inflection point where it’s time to look beyond legacy SD-WAN. The sheer volume of cloud applications and IoT devices has exploded and legacy SD-WAN solutions with controls based on application-centric policies are not enough, especially if the specific SD-WAN solution lacks zero trust principles. The evolving enterprise now needs zero trust-enabled, context-aware SD-WAN to provide fast, reliable, and secure access to any application and device at any location with full visibility and the right set of controls. This is possible using contextual policies that include understanding applications, application risks, user, user risk, device, and device risk, all of which make network operations more intelligent and more secure.
Legacy SD-WAN can’t deliver the right controls.
Limitations include the following:
- Limited number of applications can slow innovation– Having a limited number of applications a SD-WAN solution can support can hamstring a business’ ability to innovate and stand out from the competition. Legacy SD-WAN was designed to manage 3,000-4,000 applications, but this is now only a fraction of the number of applications that exist on web and cloud, which exceed multiple tens of thousands.
- Manual configuration is an operational nightmare – SD-WAN promised to deliver software-defined configuration, management, and monitoring—and it delivered on those promises. However, assigning traffic prioritization priorities to all supported applications remains a big challenge. Network operations teams need to configure these applications manually one at a time, which is an extremely slow and error prone process, and doesn’t scale for tens of thousands of applications
- Without visibility there is no control – Visibility and control are two sides of the same coin. If you can’t discover applications, how can you control them? Without having full visibility into all applications, how do you identify sanctioned applications vs unsanctioned applications that are hogging your precious WAN bandwidth and build the right controls? SD-WAN solutions must account for this balance.
- Users and devices can pose a big risk to WAN transformation – Enterprises must address connectivity and security for traditional corporate workers as aggressively as they did for remote workers. Organizations relying on traditional SD-WAN at the branch can’t get visibility and additional context into users and devices. This visibility and context can bring discoveries around users and devices into the SD-WAN policy and build better controls. Without context, is there a strategy for quarantining a visiting user that has an unmanaged device and can pose a security threat? What about micro-segmenting IoT devices at the edge as they become compromised and provide a path into the enterprise network? These questions quickly become limitations.
A zero trust, context-aware solution to the rescue
To overcome these challenges, Netskope today offers the industry’s most innovative, context-aware SD-WAN. Context-awareness for Borderless SD-WAN comes from the Netskope Zero Trust Engine, which decodes thousands of apps and cloud services to understand content and context, including application and application risks, device and device risks, and user and user risks. This unique solution solves the major challenges of legacy WAN, including:
- Run efficient operations while supporting Industry’s highest number of applications: The Netskope Borderless SD-WAN solution supports a database of 60,000+ applications. IT administrators are not going to configure QoS policies for these applications one at a time, so Netskope also rates every application with a Cloud Confidence Index, which offers an enterprise-readiness score of an application. Out of the box Netskope supports smart QoS defaults based on Netskope CCI scores used as a smart default. This takes all the manual labor away from the network operations team and results in much more efficient operations. (For example, Zoom has a CCI of 82, that is marked as a high priority by default and SureVoIP has a CCI of 38 treated as low priority out of the box.)
- Protect your organizations while managing devices and device risks: Legacy SD-WAN does not provide visibility into IoT devices, and with IoT proliferation this has become more important than ever. Netskope’s context aware capabilities can extend to automatically detect all IoT devices, managed and unmanaged, and micro- segment to manage risks that may be associated with a compromised device. For example, an IoT device, like a camera, could be sending video to an unsanctioned application. This camera can easily be blocked through micro-segmentation to reduce the blast radius in case the IoT device is compromised and can easily be remediated.
- Unify and Simplify your overall infrastructure: Traditionally, the branch level is where context has been missing, but it is now crucial to have this valuable context for granular policy controls to manage applications, devices, and users.The Netskope context sharing advantages don’t stop at the branch level either, extending to remote locations running Endpoint SD-WAN and multi-cloud networking solutions. This way both the network operations and security teams benefit from a platform that delivers a consistent policy and a unified experience with security intrinsically integrated in it. The same multi-tier management platform can orchestrate consistent zero trust policies across the branch, to the individual users, and across multiple clouds.
To learn more about the zero trust context-aware capabilities, visit our Borderless SD-WAN page, or watch the on-demand webinar “Accelerate your SASE Journey with Netskope Borderless SD-WAN,” featuring Sean Hammerle, Parag Thakore, and Muhammad Abid. Click here to contact a Netskope sales partner if you would like to arrange an Borderless SD-WAN demo.
Additionally, please read these additional blogs on related SD-WAN topics:




 Zurück
Zurück
















 Den Blog lesen
Den Blog lesen