The global pandemic caused an abrupt shift to remote work among enterprise knowledge workers, which in turn resulted in an increase in risky behavior. Attackers immediately tried to capitalize on the pandemic, with COVID-19-themed phishing emails, scams, and Trojans. At the same time, techniques used in more sophisticated cyberattacks continued to evolve. We observed shifts in the popularity of different cloud apps, with OneDrive decreasing in popularity as a malicious file delivery vehicle while other apps like Sharepoint and Box increased in popularity. Attackers also shifted techniques for initial delivery, with malicious Microsoft Office document files increasing more than six-fold to match portable executable files in popularity. This blog post highlights both of these trends as it explores the shift in the cloud apps and file types used for malicious file delivery in the past year, from September 2019 through the end of September 2020.
Cloud App Abuse
Attackers continue to abuse popular cloud apps and services to deliver malicious files to their victims in the enterprise, with more than 50% delivered through the cloud. The following bar chart compares the relative popularity of the top five apps most commonly used to distribute malicious files to enterprise users before and after the COVID-19 pandemic declaration. We measure the popularity as the number of times the Netskope Security Cloud platform blocked a user from downloading a malicious file from the app.
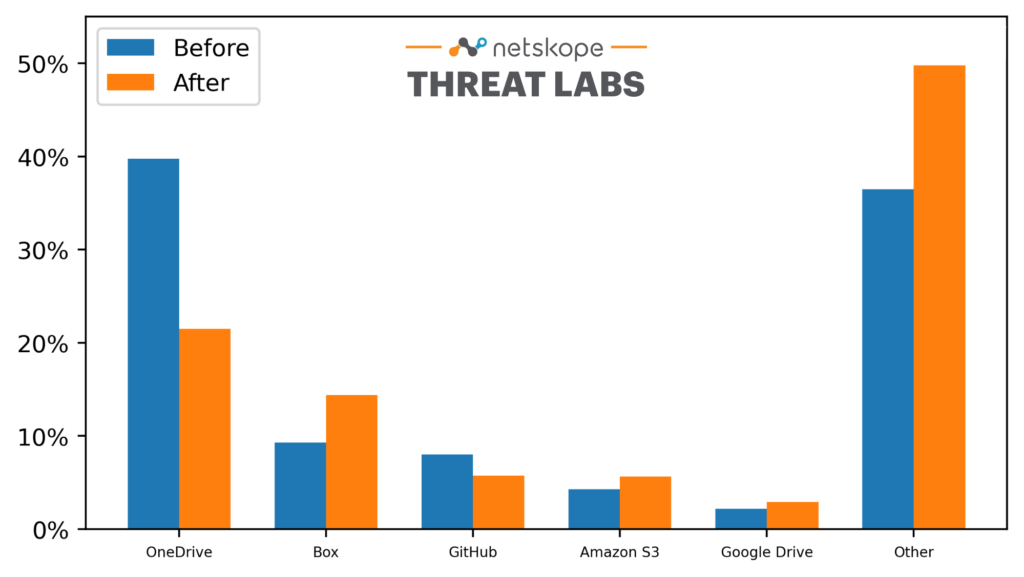
The relative popularity of the top five cloud apps for malicious file distribution remained unchanged before and after the pandemic. OneDrive saw the biggest decrease in popularity while Box saw the biggest increase. Meanwhile, the total share of malicious files distributed by the top five apps decreased during the pandemic. “Other” represents some 168 other apps, including DropBox, Gmail, Yahoo Mail, and Outlook.
File Types
More drastic than the shift in apps used to distribute malicious files was the shift in file types. The following bar chart compares the relative popularity of the top five file types most commonly used as Trojans and downloaders against enterprise users before and after the COVID-19 pandemic declaration. We measure the popularity as the number of times the Netskope Security Cloud platform blocked a user from downloading malicious files of that type, which we identified using libmagic.
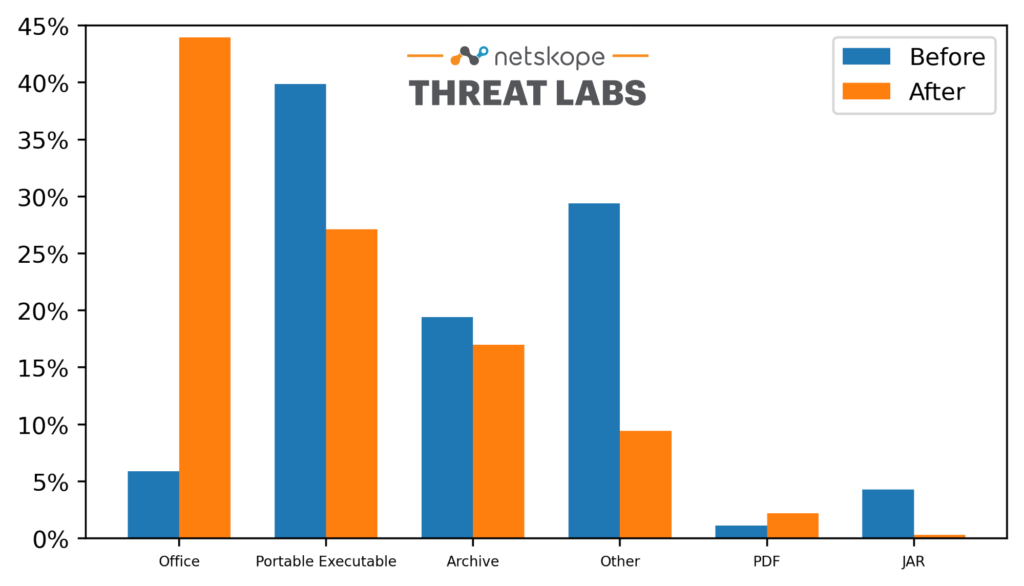
In the six months prior to the COVID-19 pandemic, Microsoft Office files accounted for only 5% of the Trojans and downloaders detected on the Netskope Security Cloud platform. After COVID, especially when Emotet became active again, we saw that percentage increase to nearly 45% while portable executable files and other types decreased. “Other” includes other executable formats, browser extensions, and scripts. Microsoft Excel files—typically containing malicious links, VBA scripts, or PowerShell scripts—account for three-quarters of the malicious Office documents we detect. More than 90% of the malicious Office documents are distributed through cloud apps, compared to 50% of all other malicious file types.
Data Analysis
The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
Conclusions
Over the past six months, attackers have shifted both the apps and the types of files they are using to target victims. Most alarming is a shift to using malicious, cloud-delivered Microsoft Office documents—predominately Microsoft excel files—signaling that attackers are having success with these methods. While this shift occurred during the COVID-19 pandemic, we do not believe it was related to the pandemic itself. Instead, we believe it to be just another way that attackers are shifting techniques to evade detection. We expect that the increased use of malicious Office documents will continue in the near to medium term. For more about recent trends in cloud adoption and security threats, please refer to our August 2020 Cloud and Threat Report.




 Back
Back
















 Read the blog
Read the blog