Summary
Starting on February 2 at around 16:00 UTC, Netskope Threat Labs was alerted to a spike of users across 48 different organizations clicking on tech support scam links hosted in Azure Blob Storage. All of the victims were located in the U.S. and distributed across multiple industries, including healthcare, manufacturing, and technology.
Every visit to one of the tech support scam sites started with a click on a malicious ad in the Bing search results. The search terms leading to the malicious ad were simple, innocuous ones, like “amazon.” This serves as a reminder that directly navigating to a website is always more secure than searching for it. If you navigate to Amazon.com directly, you never risk clicking on a malicious ad or the wrong search results. Clicking on the malicious ad sent the victims to highswit[.]space, a newly registered domain hosting an empty WordPress site, which then redirected them to one of the Azure Blob Storage containers, which served a typical tech support scam site as seen below.
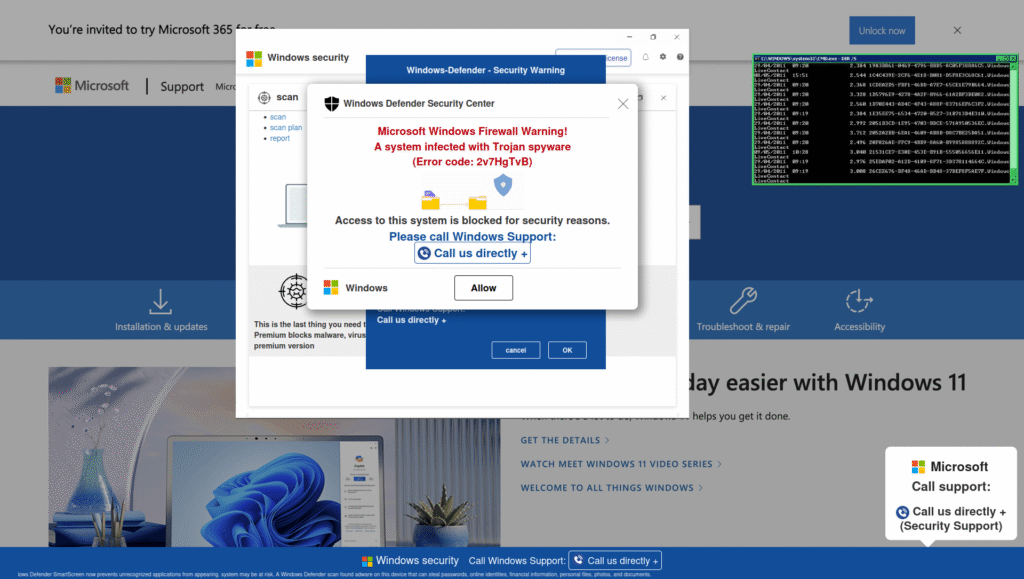
While tech support scams are not a new threat—Netskope Threat Labs has previously documented scams exploiting platforms like DigitalOcean and StackPath—this particular instance stands out. Its successful placement as an ad within Bing search results has resulted in a notable volume of clicks originating from our customer base.
Key Findings
- Widespread impact: The tech support scam campaign had a significant initial impact, affecting users across 48 different organizations in the U.S. within a short timeframe. Victims were identified across multiple sectors, including healthcare, manufacturing, and technology.
- Search ad vector: The scam’s initial vector leveraged malicious ads in Bing search results for simple, innocuous queries (like “amazon”) to redirect users. This highlights the risk of malicious advertising and searching for well-known sites.
- Abuse of cloud storage: The final scam pages were hosted in Azure Blob Storage containers. All of the malicious URLs followed a consistent pattern, indicating a standardized deployment method for the attack infrastructure.
URL Patterns
All of the URLs followed the same pattern:
xxxxxxxxxxxxxxxxxx.blob.core.windows.net/yyyyyyyyy/werrx01USAHTML/index.html?bcda=1-866-520-2041
xxxxxxxxxxxxxxxxxx.blob.core.windows.net– An Azure Blob Storage containeryyyyyyyyy– A random stringwerrx01USAHTML/index.html– Always the same string in every instance we have seen over the past two daysbcda=1-866-520-2041– The phone number that the victim is instructed to call
The phone numbers that the victims were instructed to call were:
- 1-866-520-2041
- 1-833-445-4045
- 1-855-369-0320
- 1-866-520-2173
- 1-833-445-3957
The full list of the Azure Blob Storage container domains discovered so far includes:
2222wny78new832zzz[.]blob[.]core[.]windows[.]net
222oo78new832zz[.]blob[.]core[.]windows[.]net
222y78new832zz[.]blob[.]core[.]windows[.]net
222ynew9983zzzzz[.]blob[.]core[.]windows[.]net
2299iz8ynew9983z[.]blob[.]core[.]windows[.]net
2299zzynew345[.]blob[.]core[.]windows[.]net
22ii98zew9983zxz[.]blob[.]core[.]windows[.]net
22nmynew9983zz[.]blob[.]core[.]windows[.]net
22uiz889992nnzzaazz[.]blob[.]core[.]windows[.]net
22zz78new832zzzz[.]blob[.]core[.]windows[.]net
22zzew9983zxzzz[.]blob[.]core[.]windows[.]net
22zzny78new832zz[.]blob[.]core[.]windows[.]net
22zznynew3778zzzzz[.]blob[.]core[.]windows[.]net
22zzynew9983zz[.]blob[.]core[.]windows[.]net
22zzzmnz77993zz[.]blob[.]core[.]windows[.]net
22zzzwjj8new832zzzz[.]blob[.]core[.]windows[.]net
23888zynew345[.]blob[.]core[.]windows[.]net
2uuii92mynew9983zz[.]blob[.]core[.]windows[.]net
2zzz3328new832zz[.]blob[.]core[.]windows[.]net
2zzzy78new832z29[.]blob[.]core[.]windows[.]net
33zzy78new832zzzz[.]blob[.]core[.]windows[.]net
778zzzew9983[.]blob[.]core[.]windows[.]net
788znew9983zzzzzzz[.]blob[.]core[.]windows[.]net
a99w82nz77993zz[.]blob[.]core[.]windows[.]net
auaizaz788zjzzsds[.]blob[.]core[.]windows[.]net
axsuizasuu78zmzz[.]blob[.]core[.]windows[.]net
azazaxswdr4sss[.]blob[.]core[.]windows[.]net
eemnz77993zz[.]blob[.]core[.]windows[.]net
ggy28zy78new832zz[.]blob[.]core[.]windows[.]net
nsjxsxsdxd788bnz89zz[.]blob[.]core[.]windows[.]net
rtt772ynew9983[.]blob[.]core[.]windows[.]net
rtytz8z89z9znnzbha[.]blob[.]core[.]windows[.]net
sjj8872ny78new8e[.]blob[.]core[.]windows[.]net
sssjj8872ny78new8ezz[.]blob[.]core[.]windows[.]net
sxsjkks8xs89znm[.]blob[.]core[.]windows[.]net
sxskkxsx8s8zzaszsa[.]blob[.]core[.]windows[.]net
sxskzksx8s8zxnnx[.]blob[.]core[.]windows[.]net
t7822zz2r9nowss[.]blob[.]core[.]windows[.]net
tt22y78new832zzswzz[.]blob[.]core[.]windows[.]net
tt278new832zz[.]blob[.]core[.]windows[.]net
tt72ny78new832z29[.]blob[.]core[.]windows[.]net
tt77zzynew9983zz[.]blob[.]core[.]windows[.]net
tty2zz78new832zz[.]blob[.]core[.]windows[.]net
ty8822mynew99szz[.]blob[.]core[.]windows[.]net
tyuz788z788n2nba[.]blob[.]core[.]windows[.]net
uu28jhzynew9983zz[.]blob[.]core[.]windows[.]net
w2ony78new832[.]blob[.]core[.]windows[.]net
w33ssy78new832[.]blob[.]core[.]windows[.]net
w98982wny78new8[.]blob[.]core[.]windows[.]net
wii992ynew9983[.]blob[.]core[.]windows[.]net
ww889zew832zzswzz[.]blob[.]core[.]windows[.]net
wwi2292ynew998sooz[.]blob[.]core[.]windows[.]net
wwnynew3778z[.]blob[.]core[.]windows[.]net
wwu88nz77993zz[.]blob[.]core[.]windows[.]net
wwzzmnz77993zz[.]blob[.]core[.]windows[.]net
wyuy88znew345[.]blob[.]core[.]windows[.]net
wz878728new832zz[.]blob[.]core[.]windows[.]net
wzz433w8new832zz[.]blob[.]core[.]windows[.]net
wzzzmynew9983zz[.]blob[.]core[.]windows[.]net
xsxssakxksxs8zz[.]blob[.]core[.]windows[.]net
yu882ynew99z98[.]blob[.]core[.]windows[.]net
yy78822new9983z[.]blob[.]core[.]windows[.]net
yy822ynew9983zz[.]blob[.]core[.]windows[.]net
yy822ynew9983zzzz[.]blob[.]core[.]windows[.]net
yy882mynew99z982[.]blob[.]core[.]windows[.]net
zauuazaa788z7zaass[.]blob[.]core[.]windows[.]net
zmz77993zz[.]blob[.]core[.]windows[.]net
zyyuiz889992nnzzaazz[.]blob[.]core[.]windows[.]net
zzlll9989zzsss[.]blob[.]core[.]windows[.]net
zzy778zew9983[.]blob[.]core[.]windows[.]net
Netskope Detection
Netskope detects these tech support scam pages as ET PHISHING Microsoft Support Phish Landing Page.
Disclosures
All Azure Blob Storage container domains have been reported to Microsoft and are no longer serving any malicious content as of the publication of this post. Netskope Threat Labs will continue to track this campaign.




 Back
Back
















 Read the blog
Read the blog