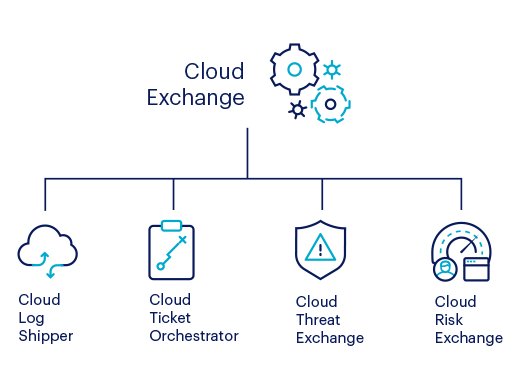
Prevent data leakage in Box
Netskope for Box can identify all instances of Box deployed throughout your organization, distinguishing between corporate and personal accounts. Netskope can determine if existing security permissions can lead to data leakage and stop it before anything happens. By enforcing risk-based governance controls and coaching users on proper use, you can ensure company-wide collaboration, while reducing risk.
Prevent data exfiltration in Dropbox
Dropbox is used by millions of people around the world to share their personal files. Businesses are now adopting Dropbox to give their employees a familiar tool for collaboration. Netskope for Dropbox helps tighten security within and between personal and business instances of Dropbox, helping you to understand and control risky activities, protect sensitive data, and stop cloud threats.
Secure access and sharing in Egnyte
With its ability to provide file access and sharing capabilities through an intuitive user interface, Egnyte gives you a great migration path to the cloud. However, improper use can still put your organization at risk. Netskope enhances Egnyte’s platform security by helping you understand and control risky activities to protect sensitive data and stop cloud threats.
Get visibility and control for your GitHub code repositories
GitHub is a cloud-based software development platform used by more than 73 million developers across 4 million organizations to host and review code and manage projects. Netskope for GitHub reduces cloud risk by enabling organizations to monitor and control user activities while ensuring only authorized personnel can access GitHub repositories.
Protect data and users in
Google Workspace
Google Workspace (formally G Suite) is rapidly becoming the primary productivity suite for many enterprises. While services like Gmail are popular with consumers, its adoption by enterprises is significant. Users often switch back and forth between their personal and business accounts, increasing the risk that sensitive company data is inadvertently leaked or purposely exfiltrated. Netskope for Google Workspace provides real-time granular visibility and control ensuring your organization is secure and compliant even when users switch between personal and business accounts.
Enforce security across Microsoft 365
Microsoft 365 is the market-leading productivity software suite used worldwide. Netskope for Microsoft 365 uniquely provides the deep visibility combined with API-enabled and real-time granular controls required to enforce data protection policies that ensure compliance and prevent data loss. Regardless of your organization’s size, Netskope can help you safely get the most out of Microsoft 365.
Safely Collaborate with Microsoft Teams
Netskope for Microsoft Teams is an advanced Cloud Access Security Broker (CASB) solution offering comprehensive protection of data and files shared between users anywhere.
Ensure data integrity in Salesforce
Enterprises of all sizes use Salesforce to give their teams an edge. Sensitive customer data and sales information can often be accessed by employees throughout an organization. Netskope for Salesforce provides visibility and security controls you need to protect sensitive data, prevent data loss and ensure compliance with regulations.
Eliminate security blindspots in ServiceNow
Organizations are adopting ServiceNow to streamline operations, increase efficiency and lower costs. However, due to its cross-functional use, ServiceNow can touch a lot of sensitive data, including personally identifiable information (PII), payment card information (PCI), and internal company information. With Netskope, you can protect your sensitive business data, while ensuring secure and compliant use of ServiceNow.
Ensure Slack collaboration is safe
Slack is a popular collaboration service, used in organizations large and small. However, while teams can easily communicate and share files through Slack, this also creates an opportunity for the inadvertent sharing of sensitive data. Netskope for Slack gives you the visibility and control you need so you can secure sensitive data and guard against cloud-enabled threats.
Secure your Workplace Deployment
Workplace by Facebook has rapidly grown as the de facto collaboration service in organizations across the world. Workplace allows employees to share, collaborate, and communicate, all in one platform. Netskope for Workplace offers granular visibility and control over Workplace, so you can secure sensitive data across your organization while enabling your employees to remain productive.




 Back
Back















 Play video
Play video






)

)